Chapter 1. Introduction
1. NATO Network-Enabled Capability (NNEC) aims to provide an environment where connected collectors, decision-makers, effectors, and information sources are integrated in a common network of networks and can be provided with, search for, or supply data and information from any location under user-adapted format and within user relevant time constraints. Advantage is taken of the great advances within civilian information and communication technology. Solutions under network-oriented concept are based on:
-
Service-Oriented Architecture (SOA)
-
Federation of systems, including federated networks.
-
Situation adapted combinations of units and systems
2. Volume 3 of this NISP will continue the evolution from platform based legacy systems to the federated Network Enabled Capabilities environment where the functionality is made generally available as "services on the net". Ultimately the goal is that the functionality of the most useful services shall be available to authorized users in each situation. The focus of this section of the volume is on the mid-term perspective having a time frame of 2 to 10 years into the future from the publication of this version of the NISP. This timeframe encompasses the realization of a fully network enabled NATO environment.
3. Within this part of the document, the focus is on the mid-term to far-term perspective. This perspective has a time frame of 2 to 10 years into the future from the publication of this version of the NISP. This time frame should encompass the realisation of a fully network enabled NATO coalition environment.
4. The purpose of this section is to identify a number of key emerging (commercial) technologies that are relevant to NATO and to provide a useful level of analysis about their possible application within military systems. While the emerging technologies discussed in this section are not exhaustive, the content of this section does draw significantly upon the technology tracking efforts of the capability team members. Once technologies are identified and their applicability analysed, then informed decisions can be made on what role each technology or standard will play in the current technical architecture. The rapid pace of technological change carries with it the potential benefits of faster and more cost-effective improvements in operational capability; however, the rapidity of change upon a broad technology front also makes the task of identifying emerging technologies particularly difficult.
5. The intention of this element of the NISP volume 3 is to be informative, whilst maintaining brevity, on a range of technologies. Consequently, the information is presented as a series of short articles that cover the essential points of interest. This flexible format is intended to facilitate the rapid change of content that will inevitably happen between issues of the NISP.
1.1. Communications & Networking
1.1.1. Disruption Tolerant Networking (DTN)
6. Disruption Tolerant Networking (DTN) are comprised of technologies that will provide network services when no end-to-end path exists through the network because of periodic or intermittent disruptions. Disruption may occur because of the limits of wireless radio range, sparsity of mobile nodes, energy resources, enemy attack, and noise. Such a robust communications network would have to be autonomic, secure and opportunistic.
7. Implications: The research in this area is principally aimed at providing internet-like services and supporting "long-haul" reliable transmission in interplanetary space, but it has applications in other environments as well. The work done to overcome delays caused by interplanetary distances can easily be appealed to tactical military networks. Distance delays are just a subset of the more general group of Disruption sources.
1.1.1.1. Bundle Protocols
8. Research goals in this area are to provide disruption tolerance by organizing information flow into bundles. These bundles are to be routed through an "intelligent" network that can manage the delivery of the bundles to the maximal extent permitted by the available topology. This method will allow messages to pass through the network with successive responsibilities, rather than the traditional end-to-end scheme. The mechanism of bundling will allow a network node to hold data if the next hop in the network is unavailable.
9. Status: The Internet Engineering Task Force (IETF) has recently published RFC 4838 and RFC 5050 to provide the common defining framework for the formation and transport of bundles of data. In 2008, the Bundle Protocol was successfully tested in space on the UK-DMC Disaster Monitoring Constellation satellite.
1.1.1.2. Licklider Transmission Protocol (LTP)
10. The Licklider Transmission Protocol (LTP) was designed to provide retransmission-based reliability over links characterized by extremely long message round-trip times (RTTs) and/or frequent interruptions in connectivity.
11. The Licklider Transmission Protocol (LTP) would replace both IP and TCP. Picturing protocols as layers in a stack, if the bottom layer is the physical wire line or radio wave connecting two devices, the Licklider Transmission Protocol sits just above that. It makes the link between two routers more reliable than IP and TCP.
12. Status: In 2008, the IRTF Working Group of the IETF established an experimental RFC (RFC 5326) on this topic
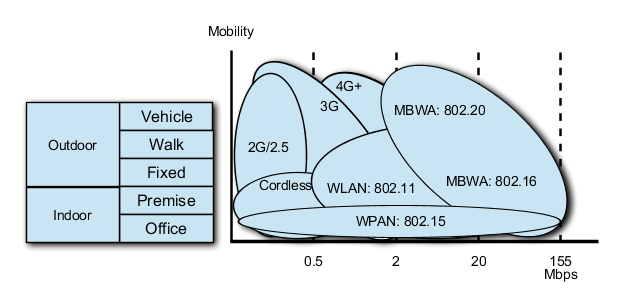
1.1.2. Wireless Networking
13. Several wireless network standards have been developed to encompass the wide range of mobile environments and applications.
1.1.2.1. Wireless Personal Area Network (WPAN)
14. A wireless personal area network (WPAN) is a computer network used for communication among computers, I/O peripherals (such as keyboards, printers, scanners, etc) and devices (such as wireless access points, cell phones and personal digital assistants) within reach of a person. The devices may or may not belong to the person in question. The range of a WPAN is typically less than 10 metres, and up to 1 kilometre under ideal conditions. WPANs can be used to replace cables between computers and their peripherals, to establish communities, or to establish location aware services. WPANs can be used for communication among the personal devices themselves (intra-personal communication), or for connecting to a higher level network and the Internet (an up link).
| Standard | Frequencies | Spectrum Type | Data Rates |
| Bluetooth | 2.4GHz | Unlicensed ISM | 2.1 Mbit/s |
| Wibree | 2.4GHz | Unlicensed ISM | 1 Mbit/s |
| ZigBee | 868 MHz, 915 MHz, 2.4GHz | Unlicensed ISM | 40-250 kbit/s |
| Wireless USB, UWB | 5GHz+ | Unlicensed UWB | 250 kbit/s |
Table 1.1. PAN Summary
15. Importance: A key concept in WPAN technology is known as plugging in. Ideally, when any two WPAN-equipped devices come into close proximity (within several metres of each other) or within a few kilometres of a central server, they can communicate as if connected by a cable. Another important feature is the ability of each device to lock out other devices selectively, preventing needless interference or unauthorised access to information.
16. Implications: Collaboration between units in the same physical area is possible. Useful on the battlefield as a method for soldier communications and monitoring.
1.1.2.1.1. IEEE 802.15.1 (Bluetooth 3.0)
17. The next version of Bluetooth, currently code named , includes a number of features to increase security, usability and value of Bluetooth. The following features are defined:
-
Atomic Encryption Change - allows encrypted links to change their encryption keys periodically, increasing security, and also allowing role switches on an encrypted link.
-
Extended Inquiry Response - provides more information during the inquiry procedure to allow better filtering of devices before connection. This information includes the name of the device, and a list of services, with other information.
-
Sniff Sub-rating - reducing the power consumption when devices are in the sniff low power mode, especially on links with asymmetric data flows. Human interface devices (HID) are expected to benefit the most with mice and keyboards increasing the battery life from 3 to 10 times those currently used.
-
QoS Improvements - these will enable audio and video data to be transmitted at a higher quality, especially when best effort traffic is being transmitted in the same piconet.
-
Simple Pairing - this improvement will radically improve the pairing experience for Bluetooth devices, while at the same time increasing the use and strength of security. It is expected that this feature will significantly increase the use of Bluetooth.
18. Bluetooth technology already plays a part in the rising Voice over IP (VoIP) scene, with Bluetooth headsets being used as wireless extensions to the PC audio system. As VoIP becomes more popular, and more suitable for general home or office users than wired phone lines, Bluetooth may be used in Cordless handsets, with a base station connected to the Internet link.
19. The version of Bluetooth after , code-named , has many of the same features, but is most notable for plans to adopt Ultra-wideband radio technology. This will allow Bluetooth use over UWB radio, enabling very fast data transfers, synchronisations and file pushes, while building on the very low power idle modes of Bluetooth. The combination of a radio using little power when no data is transmitted, and a high data rate radio used to transmit bulk data, could be the start of software radios. Bluetooth, given its worldwide regulatory approval, low power operation, and robust data transmission capabilities, provides an excellent signalling channel to enable the soft radio concept.
20. Status: On 28 March 2006, the Bluetooth Special Interest Group (SIG) announced its selection of the WiMedia Alliance Multi-Band Orthogonal Frequency Division Multiplexing (MB-OFDM) version of Ultra-wideband (UWB) for integration with current Bluetooth wireless technology. UWB integration will create a version of the globally popular Bluetooth wireless technology with a high speed/high data rate option. This new version of Bluetooth technology will meet the high-speed demands of synchronising and transferring large amounts of data as well as enabling high quality video and audio applications for portable devices, multi-media projectors and television sets, wireless VoIP. At the same time, Bluetooth technology will continue catering to the needs of very low power applications such as mice, keyboards and mono headsets, enabling devices to select the most appropriate physical radio for the application requirements, thereby offering the best of both worlds.
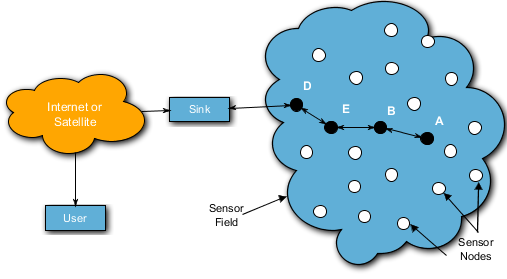
1.1.2.2. Wireless Local Area Network (WLAN)
21. A wireless local area network (WLAN) is the linking of two or more computers without using wires. WLAN utilises spread-spectrum technology based on radio waves to enable communication between devices in a limited area, also known as the basic service set. This gives users the mobility to move around within a broad coverage area and still be connected to the network.
22. Importance: Wireless Local Area Networks are more convenient, mobile, deployable, expandable, and cheaper than wired networks.
23. Implications: The wireless nature of such networks allows users to access network resources from nearly any convenient location within their primary networking environment. Initial setup of an infrastructure-based wireless network requires little more than a single access point. Eliminates the cost, time, and labour of running physical cables.
1.1.2.2.1. IEEE 802.11 (WiFi)
24. Many are familiar with 802.11, also known as WiFi, as a short-range wireless networking protocol for home and office connections. 802.11 represent a family of wireless standards. The 802.11 series has been developed by the IEEE over the past 10 years as part of the range of communications protocols under the 802 standards series.
25. Each family member is identified by a letter suffix to the series name. Currently these letters run from "a" to "w", although there is the original base 802.11 wireless standard as well. Note that there is no L standard. Some family members represent amendments (a, b, g, i) to the original standard, whereas some represents enhancements or extensions (c-f, h-j, n).
26. The 802.11 family of protocols share two common frequency bands, 2.4GHz and 5GHz, the so-called Industrial, Scientific and Medical (ISM) bands. Further more, each of these bands are divided into 14 channels. The availability of channels is regulated by nation, constrained in part by how each nation allocates radio spectrum to various services. At one extreme, Japan permits the use of all 14 channels (with the exclusion of 802.11g/n from channel 14), while at the other Spain allowed only channels 10 and 11 (later all of the 14 channels have been allowed ), to which France adds 12 and 13. Most other European countries are almost as liberal as Japan, disallowing only channel 14, while North America and some Central and South American countries further disallow 12 and 13. The emerging standards within the 802.11 family are as follows:
27. 802.11-2007: Consolidated amendments 802.11a,b,d,e,g,h,i,j with the original base standard to form the latest base standard. Status: Approved as standard in March of 2007.
28. 802.11k: Intended to improve the way traffic is distributed within a network by discovering the best available access point. In a wireless , each device normally connects to the access point (AP) that provides the strongest signal. Depending on the number and geographic locations of the subscribers, this arrangement can sometimes lead to excessive demand on one AP and underutilisation of others, resulting in degradation of overall network performance. In a network conforming to 802.11k, if the AP having the strongest signal is loaded to its full capacity, a wireless device is connected to one of the underutilised APs. Even though the signal may be weaker, the overall throughput is greater because more efficient use is made of the network resources. 802.11k and 802.11r are the key industry standards now in development that will enable seamless Basic Service Set (BSS) transitions in the WLAN environment. Status: Still in draft form, but expected to be ratified in 2008.
29. 802.11n: Focuses on improvements on the 802.11 standard to obtain data throughput of at least 100Mbps, improved coverage, and longer range. Such advances will be achievable through multiple-input/multiple-output (MIMO) communication. MIMO uses multiple radios simultaneously transmitting and receiving different signals to and from at least two radios on the client side to and from two or more on the access point. Status: Expected to be ratified in 2009. There are still some interoperability issues. There are many products available based on the pre-draft standard.
30. 802.11p: "Wireless Access in Vehicular Environments (WAVE)" - Wireless communication between fast moving vehicles or between a fast moving vehicle and a stationary object. This standard supports speeds of minimum of 200km/h and ranges of up to 1km. It uses 850-5.925 GHz band and defines enhancements to 802.11 required to support Intelligent Transportation Systems (ITS) applications. The vision is for nationwide network that enables communications between vehicles and roadside access points or other vehicles. Such networks would enable toll collection, vehicle safety services, and commerce transactions via cars. Status: Expected to be ratified in 2009. This standard would be the foundation for projects like the Communications, Air-interface, Long and Medium range (CALM) system in Europe, and Dedicated Short Range Communications (DSRC) in the United States.
31. 802.11r: "Fast Roaming" - This proposed standard will specify fast Basic Service Set (BSS) transitions that address the faster transfer of a station from one access point to another. Faster transitions are essential to support real time applications such as VoIP ("voice over IP", or Internet-based telephony) via mobile phones designed to work with wireless Internet networks, instead of (or in addition to) standard cellular networks. This will permit connectivity aboard vehicles in motion, with fast handoffs from one base station to another managed in a seamless manner. Handoffs are supported under the "a", "b" and "g" implementations. Status: Ratified and published in July of 2008.
32. 802.11s: "Mesh Networking" - Wireless Distribution System (WDS) protocol that is able to auto-configure paths between APs.
33. 802.11u: "Inter-working with External Networks" - The primary focus is on inter-working with cellular networks. Status: Ongoing; still being evaluated.
34. 802.11v: "Wireless Network Management" - Management (monitoring, configuring, updating) of attached stations through layer 2. It is to complement 802.11k that gathers information from the stations.
35. 802.11y: "3650-3700 MHz Operation in the U.S" - This amendment to 802.11-2007 would allows WiFi "like" equipment to operate at higher power levels with a range of up to 5 kilometres in the United States. It introduces three new concepts to the 802.11-2007 standard: Contention Based Protocol, Extended Channel Switch Announcement, and Dependent Station Enablement. Even though the current form is specific to operations in the United States, care was taken so that, if the light licensing concept was well received, it would not be necessary to start the 3+ year task group process in order for 802.11y devices to operate in other countries or in other frequency bands. As a result, lightly licensed 802.11 devices will be able to operate in any 5, 10, or 20 MHz channel that regulators make available by simply adding entries to the country and regulatory information tables in Annex I and J of 802.11. Has implications in the following areas: Back haul for Municipal Wi-Fi networks, Industrial automation/controls, Campus/Enterprise networking, Last Mile Wireless Broadband Access, Fixed Point to point links, Fixed point to mobile links, and Public safety and security networks. Status: Submitted for approval in June of 2008; Still not ratified.
| Standard | Description | Status |
| IEEE 802.11k | Radio resource measurement enhancements | Ongoing |
| IEEE 802.11n | Higher throughput improvements (e.g. MIMO) | Ongoing. Estimated ratification in 2009 |
| IEEE 802.11p | WAVE -Wireless Access for the Vehicular Environment (such as ambulances and passenger cars) | Ongoing. Estimated ratification in 2009. |
| IEEE 802.11r | Fast roaming | Ratified in July of 2008 |
| IEEE 802.11s | EWireless mesh networking | Ongoing |
| IEEE 802.11t | Wireless Performance Prediction (WPP) -test methods and metrics | Ongoing |
| IEEE 802.11u | Inter-working with non-802 networks (e.g., cellular) | Ongoing |
| IEEE 802.11v | Wireless network management | Ongoing |
| IEEE 802.11w | Protected Management Frames | Ongoing |
| IEEE 802.11y | 3650-3700 Operation in USA with wide range | Ongoing. Estimated ratification in 2009. |
Table 1.2. Emerging 802.11x Summary
1.1.2.3. Mobile Broadband Wireless Access (MBWA)
36. While many military installations have some sort of high-speed network backbone connected by fibre optic cabling, many of the buildings do not have high-speed connections to the backbone. This is because fibre-optic cabling, necessary for most high-speed communications, must first be installed in the ground.
37. Three emerging mobile data architectures have the most promise to eliminate the need for cables. In an effort to further improve mobile technology bandwidth, the IEEE 802 standards group which is already developing 802.11 (Wireless , WLAN), 802.15 (Personal Area Networks, PAN), 802.17 (Fixed Broadband Wireless Access, FBWA) has turned its attention to a new standardisation efforts on mobile broadband wireless access (MBWA).
38. As with many civil based technologies the key question is likely to be the performance of the system under stress (e.g. Interference/jamming). However, there exists a possibility of a low cost wireless network offering all IP connectivity for easy integration with other component networks, rapid base-station deployment, basic network security (allowing higher security to layer on top) and high performance to many users.
39. Importance: Installing fibres is a disruptive, costly and time-consuming process. Trenching costs become prohibitive to reach remote areas, such as transportation depots and ranges. Also, right-of-way issues and physical barriers such as lakes and historical grounds can increase the cost of installing fibre-optic cabling.
40. Implications: In the tactical world, MBWA may be well suited for quickly establishing links between temporary camps, command centres, and vehicles.
| Characteristics | Mobile Data Architectures | ||||
| 802.16e | 802.20 | HiperMAN | 4G+ | ||
| Standard Type | Open | Open | Open | Open | |
| Cell Radius | Line-of-sight | 48 km | - | 10 km | - |
| Non Line-of-sight | 3 km | - | 4km | - | |
| Cell Speed | 60 miles/hr | 250 km/hr | - | - | |
| Data Rate | Moving | < 10 Mbps | - | - | 280 Mbit/s |
| Stationary | 10 Mbps | - | 14 Mbit/s | 1 Gbit/s | |
| Peak | 70 Mbps | 1 Mbps | 63 Mbit/s | - | |
| Spectrum | < 6 GHz | - | 5.725-5.875 GHz | - | |
| Architecture | Packet | Packet | Packet | Packet/Circuit | |
| Bands | Selectable Between 2-6 GHz | Licensed Bands below 3.5 GHz | Selectable Between 2-11 GHz (Mainly 3.5 GHz) | Licensed Bands below 2.7 GHz | |
| Latency | Low | Low | High | High | |
Table 1.3. Data Architecture
1.1.2.3.1. Mobile Telephone (4G+)
41. Although the new 3G systems (mobile phone companies have invested heavily in this technology) have just been launched not long ago, many companies have already started on researching and developing on the fourth generation (4G) system. Researchers are hoping that the 4G system can reach a much faster speed, a connection speed over 100Mb per second during connection, tighter network security and also bring up the quality during communication no matter on voice or video calls. Via mobile phones, many things such as the security system, surveillance on certain items could be done easily.
42. One 4G+ standardisation effort called Ultra Mobile Broadband (UMB) is being coordinated by 3GPP2 (Collaboration between five Asian and North American standards bodies. It will improve the CDMA2000 mobile phone standard for next generation applications and requirements. The proposed system intends to employ OFDMA technology along with advanced antenna techniques to provide peak rates of up to 280 Mbit/s. Goals for UMB include significantly improving system capacity, greatly increasing user data rates throughout the cell, lowering costs, enhancing existing services, making possible new applications, and making use of new spectrum opportunities. The technology will provide users with concurrent IP-based services in a full mobility environment.
43. Status: The UMB standardisation is expected to be completed in late 2007, with commercialisation taking place around mid-2009 or early 2010.
1.1.2.3.2. High Capacity Spatial Division Multiple Access (HC-SDMA, or iBurst)
44. The HC-SDMA interface provides wide-area broadband wireless data-connectivity for fixed, portable and mobile computing devices and appliances. The protocol is designed to be implemented with smart antenna array techniques to substantially improve the radio frequency (RF) coverage, capacity and performance for the system.
45. The HC-SDMA interface operates on a similar premise as GSM or CDMA2000 for cellular phones, with hand-offs between HC-SDMA cells reportedly providing the user with a seamless wideband wireless experience even when moving at the speed of a car or train.
46. Status: HC-SDMA is being incorporated by ISO TC204 WG16 into its standards for use of wireless broadband systems in the continuous communications standards architecture, known as CALM. The IEEE 802.20 working group had adopted a technology proposal that includes the use of the HC-SDMA standard for the 625kHz Multi-Carrier Time Division Duplex (TDD) mode. Technology is available Asia, Europe, Africa, Middle East, and North America.
1.1.2.4. Ad-Hoc Networking
1.1.2.4.1. Mobile Ad-Hoc Networks (MANET)
47. A mobile ad-hoc network (MANET) is a self-configuring network of mobile routers (and associated hosts) connected by wireless links. The routers are free to move randomly and arbitrarily organise themselves. Accordingly, the topology of the wireless network may change rapidly and unpredictably. Such a network may operate in a standalone fashion, or may be connected to the larger Internet. With attributes such as minimal configuration and quick deployment make ad hoc networks appropriate for situations like disasters (natural or man-made), medical emergencies, military conflicts, etc.
48. The earliest predate the Internet and were called "packet radio" networks. These early packet radio systems were part of the motivation of the original Internet Protocol suite. Current are designed principally for military utility; examples include Joint Tactical Radio System (JTRS) and the High-Capacity Data Radio (HCDR).
49. The widespread IEEE 802.11 ("WiFi") wireless protocol incorporates an ad-hoc networking system when no wireless access points are present, although it would be considered a very low-grade ad-hoc protocol by specialists in the field. The IEEE 802.11 system only handles traffic within a local "cloud" of wireless devices. Each node transmits and receives data, but does not route anything between the network's systems. However, higher-level protocols can be used to aggregate various IEEE 802.11 ad-hoc networks into .
1.1.2.4.2. Sensor Networks
50. A sensor network is composed of a large number of sensor nodes that are densely deployed either inside an area of operation or very close to it. The sensor nodes are tiny, low-cost, low-power, self-organising and multi-functional (sensing, data processing, and communicating). Since the sensor nodes can be random deployed, such networks are ideal in inaccessible terrains or disaster relief operations
| Characteristics | Sensor Networks | Traditional Ad-Hoc |
| Communication | Broadcast | Point-to-Point |
| Node Numbers | Large | Small |
| Node Density | High | Low |
| Node ID | None | Individual |
| Failure Rate | High | Low |
| Mobility | No | Yes |
Table 1.4. Sensor vs. Ad-Hoc
51. The differences between a sensor network and a traditional ad-hoc network can be seen in Table 1.4. The protocols and algorithms used in traditional ad-hoc networks do not work well with sensor networks primarily because of the relatively large number of sensor nodes used by sensor networks.
1.1.2.5. Radio
1.1.2.5.1. Radio over Internet Protocol (RoIP)
52. Radio over IP is an method of converting analog radio signals into packets that transmited over an IP network. This capability of integrating disparate data and video signals with an IP infrasturcture could be the long disatnce hauler of short distance radio signals. With RoIP, there are no interoperability issues, all radio signals (e.g. VHF, UHF, POTS telephone, cellular telephone, SATCOM, air-to-ground) are packetized the same. Demodulation and detection of the orignal message is done after it has been transported.
53. Status: Draft standard is being developed by NIST, for the Bridging System Interface (BSI) hardware and software that enables radio gateway interoperability on a RoIP system. A half-dozen companies now offer Radio Over IP solutions. The tactical use of this technology has been demonstrated by coalition military forces in Afganistan and Iraq to protect convoys spread out across large geographic distances.
1.1.2.5.2. Radio Frequency Identification (RFID)
54. Radio Frequency Identification technology shares some similar characteristics with IP technology. IP is a remarkably flexible addressing system for information while RFID is a flexible addressing system for physical objects. RFID creates "an Internet of things" - a world of objects connected by Internet technologies. Indeed, it is possible that this new Internet of objects could significantly affect network architecture in the years to come.
55. RFID is the labelling system behind IP-enabled inventory and supply. Standard RFID tags contain three times the amount of information that can be stored in bar codes. They transmit data without contact or Line-of-sight with the reader, and can be read through dust, snow, ice, paint, or grime - conditions that render optical technologies, like bar coding, useless. Long-range tags can be read at speeds achievable by cars or trains, automated toll readers are a good example of this.
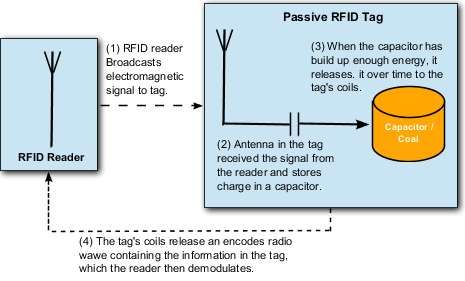
56. Capacitor / Coil (1) RFID reader Broadcasts electromagnetic signal to tag (4). The tag's coils release an encoded radio wave containing the information in the tag, which the reader then demodulates.(2) Antenna in the tag receives the signal from the reader and stores charge in a capacitor.(3) When the capacitor has built up enough energy, it releases it over time to the tag's coils.
57. Most RFID tags are passive and read-only. With a virtually unlimited operating lifetime, they consist of little more than a computer chip and an antenna. A compatible reader provides power to the tag over short distances between a few centimetres to thirty meters. The tag "awakens" and reports any information it has available to the reader. Active tags, on the other hand, are self-powered, have longer ranges than passive tags, and are constantly reporting relevant information to any reader within range. Active tags are becoming increasingly common, especially on expensive items, or cartons of items. A reader installed in a lock, for example, can automatically receive information from active tags in every vessel and shipping box that passes through. Additionally, some RFID tags are writable as well as readable.
58. Security is the key challenge with RFID. If a NATO nation implements RFID in its supply chain, and does not want other NATO nations to track its shipments and inventory, then that nation would perceive RFID technology as a significant security vulnerability.
59. Some researchers have proposed schemes that would require tags to authenticate readers, transmitting information only to authorised readers. The tags would have to store ID numbers for authorised readers, and a reader would have to broadcast its ID to the tag. To protect the reader's ID and prevent others from eavesdropping and stealing the information, the reader uses either a fixed or randomly generated number to hash (encrypt) its ID. If the tag cannot authenticate the reader's identity, the tag will refuse to transmit the information it stores. Like most security tactics, this scheme is vulnerable to attacks, such as man in the middle, or reverse engineering.
60. Importance: An advanced way to automate the tracking of people and things.
61. Implications: Improved logistics through better management of supplies and inventories.
62. Status: Because of the potential market, several vendors are actively researching security and legacy integration issues. The big challenge to RFID is its integration into existing systems. Several vendors are developing RFID middle-ware that will link new RFID systems into existing back-end infrastructures. middle-ware, for example, can help with the current lack of standards in RFID. If an organisation picks a standard that changes or loses its market prevalence, middle-ware can transform the data from readers into the format supported by back-end systems.
1.1.2.5.3. Software Defined Radio (SDR)
63. Software Defined Radio (SDR) technology uses software to modulate and demodulate radio signals. This flexible approach would solve the problem of having to carry several types of special purpose radio. Ideally, one radio could can receive and transmit a new form of radio protocol just by running new software. All functionality and expandability is built upon the Software Communications Architecture (SCA), an international open architecture framework available from the Object Management Group (OMG).
64. Importance: Reduces the need for troops to carry multiple radios.
65. Implications: Adaptable radios can solve cross-nation, and cross organisation communication interoperability problems.
66. Status: All the pieces needed to make this technology work in a tactical military environment are not ready. The biggest hurdles are form-factor, power consumption, and antenna size. Packaging such a radio that can handle every waveform used on a battlefield is daunting. Putting a 50 lb radio with a 30 foot antenna on the back of a foot solider is not practical.
1.1.2.5.4. Cognitive Radio Technology
67. Cognitive Radio technology is, when combined with Software Defined Radio technology, an effort to efficiently utilise the electromagnetic spectrum. The argument is that in any given region of the world, some portions of the spectrum are over utilised while some are underutilised. A cognitive radio will analyse the local spectrum and determine where there are spectrum "holes", or under-used spectrum. It is in these "holes" that the adaptive radio will operate by using software defined radio technology to reconfigure its broadcasting characteristics as needed.
68. The real issue is how that spectrum is managed, not the lack of available spectrum. A cognitive radio will not only analyse the spectrum usage, but negotiate usage with nearby devices. Compare the scheme to a driver's reacting to what she sees other drivers doing. If you are in a traffic lane that is heavy, maybe it's time for you to shift to another lane that is not so busy. When shifting lanes, however, a driver needs to follow rules that prevent her from bumping into others.
69. The MAC layer of the IEEE 802.22 wireless standard will be based in Cognitive Radio Technology. It needs to be also able to adapt dynamically to changes in the environment by sensing the spectrum. The MAC layer will consist of two structures: Frame and Superframe. A superframe will be formed by many frames. The superframe will have an SCH (Superframe Control Header) and a preamble. These will be sent by the BS in every channel that it's possible to transmit and not cause interference. When a CPE is turned on, it will sense the spectrum, find out which channels are available and will receive all the needed information to attach to the BS. Two different types of spectrum measurement will be done by the CPE: in-band and out-of-band. The in-band measurement consists in sensing the actual channel that is being used by the BS and CPE. The out-of-band measurement will consist in sensing the rest of the channels. The MAC layer will perform two different types of sensing in either in-band or out-of-band measurements: fast sensing and fine sensing. Fast sensing will consist in sensing at speeds of under 1ms per channel. This sensing is performed by the CPE and the BS and the BS's will gather all the information and will decide if there is something new to be done. The fine sensing takes more time (approximately 25 ms per channel or more) and it is utilized based on the outcome of the previous fast sensing mechanism. These sensing mechanisms are primarily used to identify if there is an incumbent transmitting, and if there is a need to avoid interfering with it.
70. Importance: Enables efficient usage of available limited spectrum.
71. Implications: Ideal companion technology to Software Defined Radio Technology.
72. Status: Approved by IEEE in january of 2008, the 802.22 standard is the first wireless standard based on cognitive radios.
1.1.3. Wired Networking
73. When compared to wireless networking, the more mature wired networking area provides benefits in cost, reliabilty and performance.
74. Implications: The need for wired networking will be dictated by the operational environment.
1.1.3.1. Fibre-Channel over Ethernet (FCoE)
75. Fibre-Channel over ethernet allows Fibre-Channel devices to connect with one another over ethernet based networks. With FCoE, native Fibre-Channel frames are encapsulated into ethernet frames to be sent over a 10-Gbit Ethernet network. Considered a low-cost, high performance alternative to Fibre-Channel over long distances. The main applications that benifet from this technology are sStorage Area Networks (SANs). With FCoE, network (IP) and storage (SAN) data traffic can be consolidated using a single network switch. This consolidation can:
-
reduce the number of network interface cards required to connect to disparate storage and IP networks
-
reduce the number of cables and switches
-
reduce power and cooling costs
-
increase utilization of servers through server virtualization technologies
76. Status: Not yet apporved as a standard by INCITS, InterNational Committee for Information Technology Standards organisaton, but several vendors are shipping products that will support the future standard. Expected to be ratified in late 2009 or early 2010.
1.1.4. Transport Layer
1.1.4.1. Stream Control Transmission Protocol (SCTP)
77. The Stream Control Transmission Protocol operates on top of the Internet Protocol (IP), and is defined in the RFC 2960 (IETF standard). SCTP was developed to provide reliable transport of SS7 messages over an IP network.
78. The Stream Control Transmission Protocol (SCTP) is a new IP transport protocol that operates on top of the Internet Protocol (IP), and is defined in the RFC 2960 (IETF standard). It exists at an equivalent level with UDP (User Datagram Protocol) and TCP (Transmission Control Protocol), which provide transport layer functions to many Internet applications.
79. Like TCP, SCTP provides a reliable transport service, ensuring that data is transported across the network without error and in sequence. Like TCP, SCTP is a session-oriented mechanism, meaning that a relationship is created between the endpoints of an SCTP association prior to data being transmitted, and this relationship is maintained until all data transmission has been successfully completed.
80. Unlike TCP, SCTP provides a number of functions that are critical for telephony signalling transport, and at the same time can potentially benefit other applications needing transport with additional performance and reliability.
81. Status: SCTP has been approved by the IETF as a Proposed Standard. The error check algorithm has since been modified. Future changes and updates will be reflected in the IETF RFC index. SCTP has been implemented on several OS: Windows XP, Linux, AIX, BSD, Solaris, and QNX Neutrino.