1.6. Security
153. There is an explosion of protocols and standards dealing with identities. These range from identity, authentication, access control, compliance, workflow, policy, storage, etc. From these protocols and standards we are seeing infrastructure that is being developed to support them. There is a growing trend to provide security infrastructure openly so that there is interoperability and collaboration in the "Security Environment". From this infrastructure many applications will be written, such as signal sigon.
154. Implication: For an enterprise, this means a lower cost of password and account management, and lower user frustration by allowing users to control of their login.
1.6.1. Authentication
1.6.1.1. OpenID
155. OpenID is a decentralised single sign-on system. Websites using OpenID allow web users to abandon the need to remember traditional authentication tokens such as user name and password. Instead, they only need to be previously registered on a website with an OpenID "identity provider", sometimes called an i-broker. Since OpenID is decentralised, any website can employ OpenID software as a way for users to sign in; OpenID solves the problem without relying on any centralised website to confirm digital identity.
156. Status: OpenID is increasingly gaining adoption among large sites, with organisations like AOL acting as a provider. In addition, integrated OpenID support has been made a high priority in Firefox 3 and Microsoft is working on implementing OpenID 2.0 in Windows Vista. A non-profit organisation,OpenID Europe, was created in 2007 to support and promote the OpenID framework in Europe.
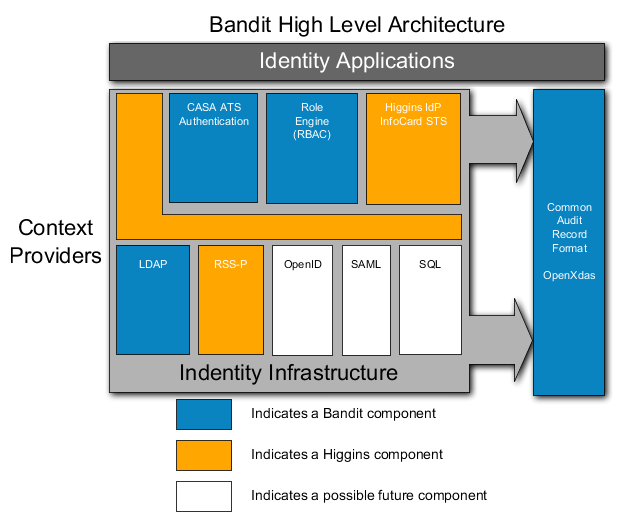
1.6.1.2. Bandit Project
157. The Bandit project is a worldwide open source community that enables open yet secure enterprise computing through an Open Identity System. Bandit's components will create an environment where, the right people get the right access to the right IT systems at the right time. The Bandit project is sponsored by Novell, which contributes significant engineering, management and infrastructure resources. Novell, in consultation with the Bandit community, sets the project engineering goals and retains ultimate responsibility for the project.
158. Bandit's current emphasis is in the following areas:
-
Provide simple application access to multiple identity stores
-
Support multiple and pluggable authentication methods to provide consistent application access
-
Provide a simple application interface to unify system access based on roles
-
Allow applications to easily participate in a common compliance system
159. Status:Work is being done on version 2 of the Common Identity component and the Role Engine component.
1.6.2. Risk Analytical Engines
160. Risk Analytical Engines are used predict risk based on models. Risk assessments are done real-time.
161. implications: Risk Analytical Engines are used in a variety of industries such as financial, health, and customer service. But it is the potential use in enterprise identity management and network intrusion detection that makes it an attractive technology category.
1.6.2.1. Predictive Model Markup Language (PMML)
162. Predictive Model Markup Language (PMML) describes predictive analytical models that are conventionally used to analyse data in a data warehouse. PMML provides a method for systems, or computer programs to access an analytical model by providing a web services abstraction of the analytical model. This allows the invocation of the analytical model hosted by an analytic engine through a web services interface to the analytic engine. Invocation of the analytical model through the web services interface may be independent of the analytic engine hosting the analytical model.