B.2. National Network Enabled Efforts
65. As stated previously NNEC is based on national initiatives. Many NATO and Partner Nations have initiated network enabled programs in their respective nations. NNEC will be a federation of NATO and National service based systems, with the Nations contributing around 90 percent of the capabilities, it is important that the standards and profiles described in the NISP take into account the ongoing developments in the nations.
B.2.1. Finland
66. The C4 development started in Finland in the 1980's. At that time, all systems were developed separately for the Army, Navy, and the Air Force, thus resulting in a situation with a large number of distributed stove-piped systems. Although these systems have served us well in the past, their lifecycle is coming towards an end, and new systems need to be developed to serve our current and future needs. We face the same challenges as many other militaries as we realize that it is not affordable to develop new systems on top of the old ones by patching and bridging gaps. Furthermore, there is a limit to which technical, data, and application integration can take us. Therefore we have decided to give up most of our old systems by 2010. This decision became the starting point for the development of our IC4I and forms the basis for our Network Enabled Defence (NED), which comprises a domestic roadmap to which crisis management is aligned.
67. The Finnish view on NED is that it is a working title for a concept that uses the principles of Network Enabled Capabilities for providing total defence (also called homeland security). Finland has a long tradition in total defence, where the armed forces cooperate with other governmental agencies and industry to secure the functions vital to the society. NED is defined to describe how future networks with improved and integrated information and weapon systems can enable command and control in joint and territorial operations with multiple partners. The basic requirement in our system development is interoperability with the international development. Thus, there is no significant difference whether the crisis is in Finland or somewhere else, nor is there a technical difference whether the coalition is lead by the UN, EU, NATO or a nation.
68. The Finnish approach to NED is very pragmatic and based on incremental development. We place high emphasis on innovation opportunities that are technically feasible, cost-efficient, and organizationally achievable. NED is not seen as a goal, but as a journey in the right direction together with partners. Especially industry partnerships are considered valuable, as they have the research and production capabilities needed to turn innovations into solutions and applications - again, real implementations, not just visions and theories. One example of such partnership is the establishment of a Network Centric Operations Centre of Excellence (NCO CoE) together with IBM in Finland.
69. The first task that we did was to rationalize system development in order to cut the number of overlapping systems. This lead to system centralization, and the idea of "the network as the computer" emerged, which in practise means that thin clients capable of doing local processing are used, but the applications and data storage are performed via the network. We also decided to take a leap into a SOA-based approach. The two main issues in this first phase are the reliance on COTS as well as our architecture development. In our architecture development, we have found the usage of overarching and reference architectures as drivers for change, and ended up with an overarching architecture and two reference architectures (C4I and administrative). In the near future, there will be two additional reference architectures, which are shared with other agencies for collaboration purposes. As for using COTS, we have taken a very pragmatic approach in building and deploying our systems. For example, for voice communication we have developed a TETRA based system, which was gradually deployed in Finland as well as in international exercises and operations, such as in the Finnish battalion in Kosovo (2002), the Nordic PfP Exercise (2003), MN Brigade (C) in Kosovo (2003), and MN TF Althea (2004). During the years 2001-2004 we developed civilian crisis management systems, which were based on the idea that whatever can be deployed in our national defence can be used in international operations as well. Another developed COTS product was the Deployed COTS Network (DCN), which connects virtually any digital and analogue network together. In less than four months we procured, tested trained, and deployed a brigade level DCN to KFOR.
70. The second step involves a functional change and is concerned with information sharing. At this stage, SOA is used as the basis for the architecture. At the moment, we have three main experiences developed or in development for the second phase. One is the Network Enabled Operations Centre (NEOC), where we tested the centralization of information powerhouses into the core network. The concept of information powerhouses basically means that all information is centralized into a few server hotels, which are connected to the backbone and accessible through the access networks. The demonstrator proved increased survivability, better situational awareness, and brought new processes and a new C4 structure. The second issue is SECNET, the interagency networking concept. This is still under development, but we are getting there in a pragmatic way, developing services that can be shared between authorities. The third concept is METO, which is a Sea Surveillance Information System (SSIS) shared by the Navy, Border control, and Maritime traffic safety, and thus coordinated by the defence ministry, ministry of transportation, and the interior ministry.
71. In the third phase, we are concerned with a cultural change that involves collaboration based on the SOA approach. To mention two examples, we have build proof-of-concepts for a joint Common Operational Picture (COP) service. In the first PoC, we tested the scalability of having a "mother database" with all information. This database was reachable from the Defence Staff through a common portal. Information was collected from various local environments, which all had a picture of their own environment. The PoC showed us that the technology worked. In the second PoC, we tested what we call the "child's architecture", where some of the local environments are detached from the "mother environment". The idea is that the detached unit is able to operate on its own even without a network connection, seeing only its own environment. However, as the network connection is resumed, it should be possible to rejoin to the common environment. The focus was on the scalability of SOA, information handling when coming back online, and integrity issues. In this PoC we scaled down to brigade and battalion level, but it is possible to scale it further down to team or even individual fighter level.
72. We have learnt many lessons on our still ongoing journey towards NED. We believe that our pragmatic and incremental approach together with strong industrial partnership, where development and deployment lifecycles can be brought down to 18 months, is a good way to go ahead. Collaboration with NATO in architectural development, using the idea of overarching and reference architectures, and working together on open service interface descriptions has proven valuable. Also testing the systems in exercises and deploying them on the field in various operations have given us a lot of experience.
73. Still, several challenges remain. The main challenge is IA, which often is a hot potato that nobody wants to address. This is the next challenge that we will really focus on solving. The IA challenge is especially difficult at the moment due to the cultural change related to the transition from "need to know" to "need to hide" and "duty to share". Whereas communication security has been addressed by various security protocols, network and content security are still open questions. For example, the concept of CBIS/MLIS has suffered from a standstill for several years.
74. Another challenge is the difficulty in integrating differ nt approaches from NATO, EU, the government and industry. However, we are hoping that the industry will help us solve the problem, and hence we will continue with our strong partnership approach. Furthermore, future services are still unknown, thus leading to "ad hoc system design". The best we can do at the moment is to try to develop a common and generic environment, in which to fit future services in a standard way. Also decomposing current systems to services provided by applications using core and common services is a challenge.
75. The biggest challenge, perhaps, is not technical, but cultural. The user needs to feel "a return of investment" for his efforts to learn new ways of doing business. Training and educating users is one thing, but the real challenge is to get people to truly adopt the concept of collaboration in a network-centric environment using unified process workflows.
B.2.2. France
B.2.2.1. Background
76. The objective of the present document is to describe the French orientations to rationalize the interconnection between the French CIS and NATO CIS.
B.2.2.1.1. France involvement in NATO force structures
77. France is involved in many NRF rotations:
-
2006 : NRF7 French participation in the Eurocorp at LCC level
-
2008 : NRF10 MCC
-
2008 : NRF11 LCC
-
2009 : NRF12 JFACC
-
2009 : NRF13 CJSOTF
-
2010 : NRF14 MCC and LCC (Eurocorp)
78. Besides, France has already 2 HRF HQ located in France: a maritime HQ in Toulon (southern part of France) and a LCC HQ in Lille (northern part of France).
79. Each time France is on alert for HRF or NRF purposes, it is mandated to setup a special interconnection between NATO HQ and these headquarters. In order to optimise those interconnections from a personnel perspectives and a cost point of view (equipments, leased lines..), the intention is to setup a permanent network. Furthermore, this permanent network will facilitate the exchange of information with NATO and will enable France to be in line with the NNEC perspectives to offer the available services to all the military users.
B.2.2.1.2. French participation in NRF5
80. France has participated as the JFACC during the NRF5 rotation. That was the starting point of the rationalisation work which is made in the logical continuity from this participation. The Figure B.3 displays the roles played by the French units and the information systems involved during the certification exercise ALLIED ACTION 05.
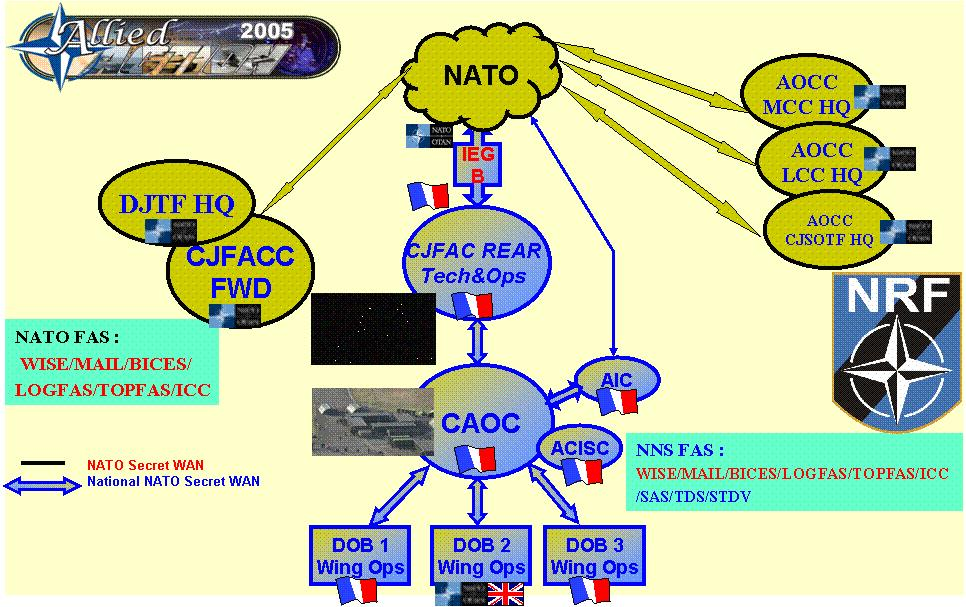
Figure B.3. French participation in Allied Action 05
81. The French systems used during this exercise were the following:
-
SCCOA (command and control system for air operation)
-
Document management system
-
STRADIVARIUS : French integrated air picture
-
IRIS : AdatP3 formatting tool
-
TDS : friendly force awareness
-
Messaging system
-
Videoteleconferencing
82. The Lessons learnt from NRF5 participation can be sorted in three points:
-
First of all, from the user's point of view, for maximum efficiency it would be easier to have only one workstation to access directly to the right information instead of using a swivel chair and disquettes (or USB keys). Another aspect of this point of view is to adopt the maxim "train as you fight", and as such it is highly desirable to have the ability to use NATO and French tools on the same network.
-
From CIS engineers' point of view, the complexity the Information Exchange Gateway (IEG) imposes the need for a specific CIS team dedicated to the support of this gateway. It is not easy to deploy and configure it. On the other hand, using only one IP network between NATO and France has eased the overall deployment. The compromise that should be made is to avoid the deployment of those gateways on theatre where the skilled human resource is rare.
-
From the interoperability point of view, it is much easier to have only one network to enable people to access the services they need.
B.2.2.2. Situation today
83. The actual situation is the result of successive deployment made when the different systems were available. Each time the participation of a French unit was required an extension of the NATO system was establish to connect them. The result is that each functional system has added direct link and specific network to enable the required exchange of information. The number of transmission links has grown and equally the number of gateways and crypto devices. One of the links might be overloaded at a period of the day but we are not able to use another link that might be free at the same time. The teams in charge of these equipments have no centralized management tool and no possibility to improve the quality of service for the different communities of users.
B.2.2.3. Optimization and rationalization of NATO links
84. The first step proposed is to rationalize the transmission links. For the moment, direct connections between each French location to the NATO network have been established. Hence the number of leased lines is important and to allow a communication at NATO secret level between Brest and Toulon for NATO purposes the communication is done via SHAPE. The optimization is not done on the different links and the level of redundancy for each location is relatively low. The proposed way to improve the actual situation is to:
-
Have 2 BME for permanent purposes (1 NATO Point Of Presence close to Paris and 1 for ACCS)
-
1 BME for each HRF headquarters
-
Establish 2 transmission links between Paris, Lyon and NATO
-
Create links within the French network to avoid having to go back to the NGCS for communications between 2 sites, working for NATO purposes, located in France.
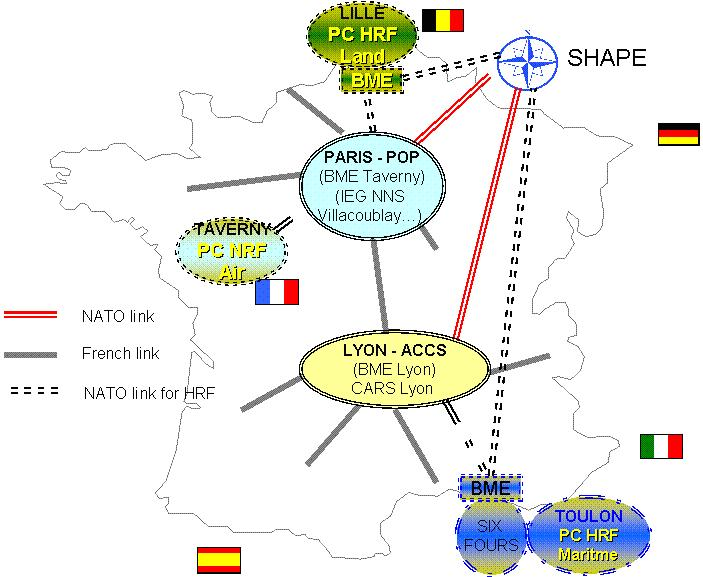
Figure B.4. Future Interconnection
B.2.2.4. Setting up of a unique logical network
85. The main objective for the NATO Secret network (FR NNS) is to give the opportunity for the end-user to have only one computer on his desk accessing all the needed services. The first step is to take into account the messaging and webaccess services to enable the access to ICC, MCCIS, BICES-webserver, WISE and CRONOS. All the "supporting" services like DNS, PKI, NTP will be available for the different systems. The flows of information between the national side and the NATO sides will be filtered in the appropriate gateway.
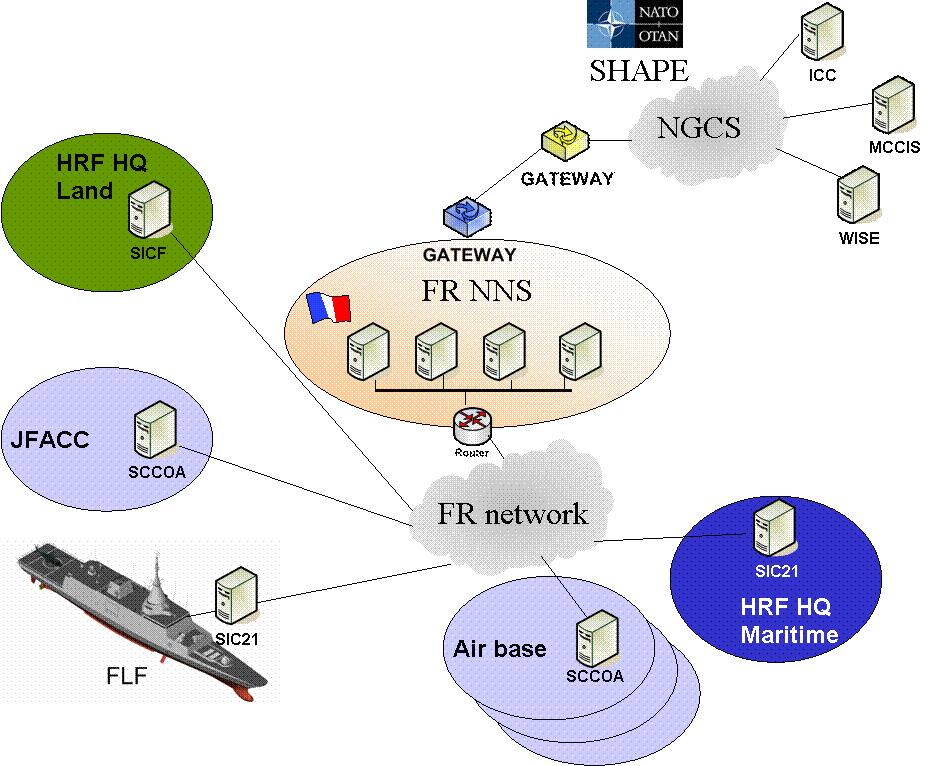
Figure B.5. IP Interconnectivity
86. The target is to share the access also for other systems like ADAMS, LOGREP, LOGDATA,..and facilitate the evolution towards NMS.
B.2.2.4.1. Short term solution
87. The availability of the FR NNS is needed for the validation phase of the new maritime system that France is developing: SIC21. This system will have to exchange information with MCCIS and several others NATO systems. As this validation phase will start during summer 2007, it is envisaged to use the IEG that was used during the NRF5 rotation with some minor changes (authorization of MCCIS flows). At the same period of time, the air community will start to move on the NNS: the CASPOA (Analysis and Simulation centre) for air operations preparation, which is a NATO Centre of Excellence, located in Taverny (close to Paris), the CCOA (Air Operation Centre) located in Lyon and the CDAOA (Air Defence and Air Operations Command) located in Paris will be connected.
88. At the end of 2008, all the ICC and MCCIS clients located in France should be able to work directly from their computers on the NNS. This means on the contrary that the people located on the theatre will still require direct links to NATO WAN.
B.2.2.4.2. Mid term objective
89. Two aspects will be considered after the starting up of this network. On one side new clients will have the opportunity to access those services and on the other side new services will be added on the network. The new clients concerned by this migration on NNS are the squadrons and air headquarters that can participate in NRF/HRF such as flying units, ARS, Ships and headquarters and the new headquarters created in France The pace for moving the units will be based on the next rotation of NRF where France is playing a component command role.
90. For NRF 11, France will be Land Component Command and still keeps two options for its interconnection. The first would be to use the FR NNS and the second to have a direct connection to NSWAN. The choice is depending on the organization of the Joint Force Command leading the rotation.
91. For the NRF 12 France, Air Component command, it is assumed that the FR NNS will be used as it was done during the rotation 5. The only difference would be the availability of more services.
B.2.2.4.3. CRONOS integration in FR NNS
92. The actual network is obsolescent. It was built in 1999 and some client workstations were deployed in various locations. France has contracted a support with a company to install and maintain the various computers. This contract is coming to its end, thus there is an opportunity to re-analyse the relevance of such a contract and the associated cost. Some clients will not be connected with the contractor because there are out of the boundary of the initial contract. France has made the decision to int grate this "service" in the FR NNS. No more upgrade of the actual network is planned; all the new users will be connected via the FR NNS.
B.2.2.4.4. ICC integration in FR NNS
93. France will use the opportunity of the movement of the different headquarters during the 2007-2008 period to setup an architecture that will support all the workstations spread out in many places in France. The upgrade of ICC from the actual version to 2.7.1, then 2.8 will give an ideal integration period to migrate towards the new approach. After that migration it is assumed that network upgrades will be necessary for the air community for the arrival of ACCS. All the network evolutions will be taken into account by the FR NNS network manager.
B.2.2.5. Ongoing work
B.2.2.5.1. Interfaces between NS, NNS and MS
94. During operations, usually a Mission Secret network is deployed. To enable interconnection between network handling NATO Secret information and network handling Mission Secret information, it will be necessary to develop an IEG Case C. The location of this gateway is still under discussion and need to be further investigated. The main objective for this interconnection is to offer all the NATO IP services to the different communities of interest in the theatre.
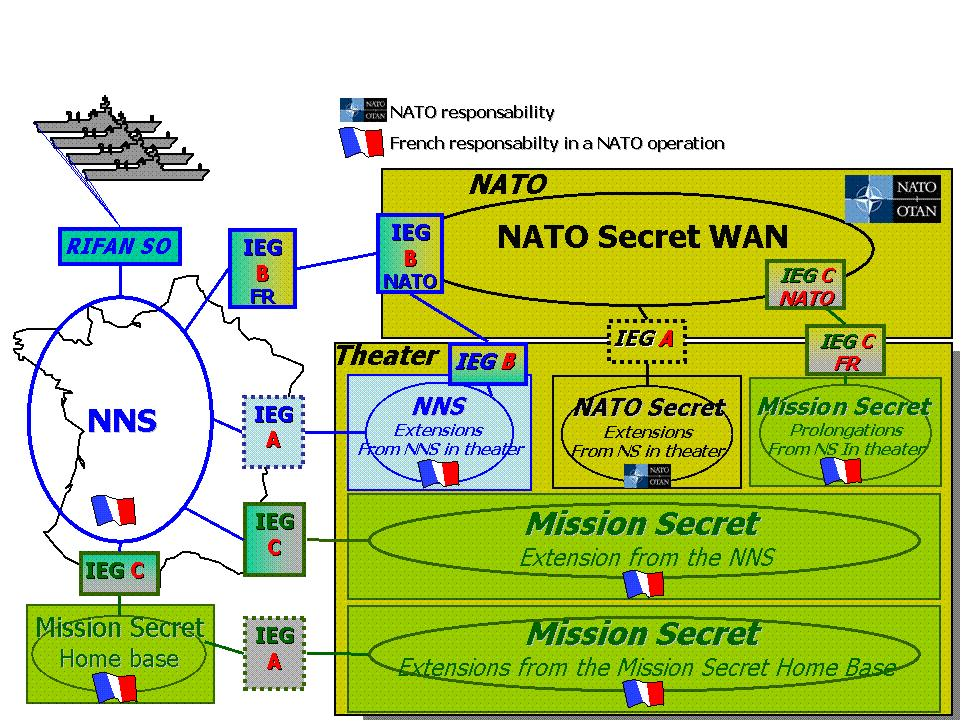
Figure B.6. Interconnecting MS Network
95. The management of such a network composed of systems managed by NATO bodies and national teams will need to be worked out to develop Service Level Agreement between the network providers (NATO and national) so that availability seen from the users' point of view is maximal.
96. The other challenge will be to ease access to the right information. Having authorized the interconnection of the NATO and the national systems does not mean that the various people in the different Headquarters are accessing the information of interest to them.
B.2.2.5.2. IP networks not on NNS
97. Some systems are currently under development and a more accurate analysis must be undertaken to verify how and when they could go on the national network. That is the case for ACCS and Bi-SC-AIS. This analysis should be followed by a testing phase to ensure that the system continue to provide the services it is supposed to provide.
98. For other services, like videoteleconferencing, France will setup a separate network because of bandwidth constraints. When the quality of service will be spread on all the IP networks, and operational priorities agreed within the nations, this could evolve towards a unique network on which all the services would be made available.
B.2.2.5.3. Non IP networks
99. If there is a clear thread to use an IP network for exchanging most of the data needed for command and control functions, it must be recognize that non-IP networks will last for at least 5 years. Thus it is important for the services that they support to guarantee that the interoperability between the non-IP systems within NATO nations and PfP nations will continue until the transition phase to IP is accomplished. The services concerned are real-time service (e.g. Link 16, circuit between radar and CAOC,...), telegraphy, circuit switched and packet switched services.
B.2.2.5.4. NNEC perspectives
100. To foster and federate initiatives to improve military actions effectiveness within a coalition force, information is the key element. Information management and effect control to reach the desired end-st te have to be taken into account joint, inter-agency and international aspects development of interoperability, using state of the art methods will accelerate adaptation towards using enterprise services across the nations and appropriate networking. The necessity to accelerate the acquisition of the systems and to optimise spending will tailor the experimentation process. In order to take advantage of all the technology opportunities, a structured but pragmatic approach will be taken to enable the different program managers to take into account the interoperability challenges in an international context. In particular, studies need to be done to identify the criteria to determine when Service Oriented Architecture is the right approach and, when appropriate, propose a migration plan in accordance with the other nations involved.
Figure B.7. French Battlelab
B.2.3. Netherlands
B.2.3.1. Policy and direction
101. NEC is essential for the innovation of military operations and recognised as a priority in Defence policy. This policy is reflected in the three courses that are followed to promote the specific implementation of NEC in the armed forces:
-
Improvement of the adaptability of the armed forces for participation in multinational, joint, combined and interagency coalitions;
-
Improvement of the ability of the armed forces to innovate;
-
Contribution to the implementation of an integrated multinational NII.
102. Due to the priority given to NEC, the Secretary-General established an NEC steering group. This group is tasked with the promotion of innovation of military action by giving direction to the development of NEC. The Director of Operational Policy, Requirements and Plans of the Defence Staff provides central direction to the development of NEC and manages the NEC steering group. Nearly all parties involved in the transformation of the Defence organisation are represented in the steering group. The group is chaired by the Deputy Director for Requirements (of the Defence Staff). The tasks of the steering group include:
-
Promoting the development of innovative military concepts;
-
Promoting the adaptability and interoperability of Dutch capabilities in multinational (NATO, EU, ad hoc) coalitions;
-
Monitoring the implementation;
-
Informing and advising the civilian leadership about relevant subjects;
-
Formulating, on an annual basis, an NEC plan as an input to the Defence plan, to be able to monitor the progress in the development of NEC and to lay the foundation for future requirements; and
-
Contributing to the preparation and harmonisation of Dutch positions in meetings of relevant international consultation forums.
B.2.3.2. Implementation of national NII
103. The Netherlands armed forces will be tasked with implementing the national segment of NII, the Dutch NII, which can be integrated into larger coalitions. In this process, the main areas of attention are:
-
Design
The NII must be designed in such a way that it can support networked operations. It requires agreements on common architecture, the use of technologies and standards, but also on basic data and the management of these data.
-
Realisation
Through investment programmes and concrete projects, the NII hardware, software and services components, as well as the interfaces between those components, will be implemented.
-
Implementation and maintenance
This mainly concerns agreements and measures to ensure that the new technical possibilities are in fact being used. Everything depends on the willingness to share information. This area of attention also includes information management and control.
-
Protection
Arrangements must be agreed, measures must be taken and investments must be made to ensure the security of NII as well as the reliability of the information supply.
B.2.3.3. The development of NEC
104. NEC cannot be bought. Furthermore, the realisation of NEC is an evolutionary process without a strictly defined beginning or end. It is a process of growth, comparable to the process of change that many organisations go through in order to stay up-to-date in the field of information and communication technology. Doctrines, processes, command and control, organisations, personnel and materiel must develop in a coherent and evolutionary way. That, therefore, is the approach that the Defence organisation will use towards the development of NEC. As a result, NEC will be introduced into the Netherlands armed forces in a gradual and manageable way. This approach is characterised by the following principles:
-
combination of bottom-up activities aimed at the development of the necessary information infrastructure and top-down activities aimed at concept development with regard to the future capabilities;
-
a step-by-step approach, i.e. a learning path where experiments are used, in close cooperation with developers and users, to reduce the risks as much as possible and make users aware of the new possibilities of NEC as soon as possible;
-
co-evolutionary approach: the balance among the various aspects of development is constantly monitored.
105. For several NEC systems, the Defence organisation takes itself the lead in the development. This approach is different to the approach used by many other nations, who develop specifications and delegate the actual development to industry based upon these specifications. TITAAN and ISIS, for example, are being developed by the Dutch Army itself, with support of industry.
106. The Defence organisation distinguishes three types of innovation on the path towards NEC:
-
Technological innovation
The development, application and implementation of new technology bring about changes in the physical domain.
-
Process-driven innovation
The adaptation of organisational processes and the implementation of new operational concepts also causes changes in the information domain.
-
Organisational innovation
The structure, standards and culture of the organisation and the individual change, causing the cognitive social domain to change too.
107. Taking into consideration the three types of innovation, there are five NEC levels, if we also include the zero situation - the platform-centric level. Using these levels can help the Defence organisation define its ambitions and requirements clearly and can also provide insight into the adaptability and interoperability of a military capability. These levels are respectively Isolated (1), Deconfliction (2), Coordination (3), Collaboration (4) and Coherent effects (5).
B.2.3.4. Critical success factors for the implementation of NEC
108. Critical factors on which a successful implementation of NEC in the Netherlands armed forces will depend, include:
-
Requirements evaluation and procurement
In the processes of requirements evaluation and procurement, NEC-related requirements must be taken into account structurally. This means that attention must be paid not only to the capability that is acquired, but also to the future role of that capability and its integration in the network. Flexible and incremental procurement strategies, in which the insight into the functional demands and the best way to meet those demands gradually increase, tie in with this. This also requires a more intensive cooperation with the industry. In the development of new capabilities, NEC-requirements will be taken aboard in the design, just as is the case now with the Joint Strike Fighter.
-
Information Management development under architecture
In order to establish the Dutch NII and to steer the development of the required Information Management infrastructure in the right direction, there must be an architecture available which is used effectively. The Defence Information Management Architecture (DIVA) will be developed further for this purpose.
-
Scientific research and operational experiments
This is necessary to be able to evaluate the usability of new concepts and technologies, thus reducing the risk of making high costs that turn out to be unnecessary and irreversible choices that turn out to be wrong.
-
The development of NEC competencies and the design of C2 processes
It is clear that NEC will have a considerable impact on the human element in the Netherlands armed forces. The success of the implementation of new technology, systems and concepts and the improvements in performance that these should bring about is wholly dependent on the presence of the willingness and the competencies to actually use them.
-
Central coordination and international cooperation
The ideal situation would be that national and international agreements are made so that the various NEC processes will be able to reinforce one another. In order to achieve this, there must be central coordination and international cooperation.
B.2.3.5. Examples research and experiments
B.2.3.5.1. Experimenting - JPOW
109. CHANIA (CRETE) - In Joint Project Optic Windmill (JPOW), the computers of all participating countries are linked together, for interoperability is an integral concept throughout JPOW. "Three, two, one, fire", a Greek officer, headphones over his coalblack hair, counts down. A trembling explosion; a grey white cloud of smoke like a small cauliflower. An orange-coloured rocket races up from the launch site and hisses its way into a cloudless sky. Shortly before the projectile intercepts a small target aircraft, it is destroyed from the ground, and its shattered remains fall into the ice-blue Mediterranean waters off the coast near the NATO shooting range on the rocky island of Crete. This pandemonium is repeated three times. It is D-Day in the international air defence exercise Joint Project Optic Windmill. As a highlight, the Guided Missile Group of the De Peel airforce base shoots four ageing rockets into the firmament. JPOW is somewhere in between Star Wars, Star Trek and the US Strategic Defence Initiative. The foundation of the project was laid by the Netherlands, motivated by the first Gulf war (Source: Defensiekrant (MOD periodical), 20 April 2006).
B.2.3.5.2. Experimenting - SENECA
110. In 2005, the Defence organisation, along with TNO and THALES, carried out the first Dutch Joint NEC experiment. This experiment involved setting up a distributed experimenting environment which linked several locations together. Simulated operational sea, land and air systems successfully networked their actions in a single scenario. The experiment demonstrated the added value of the development of a Simulation Environment for NEC Assessment (SENECA) that provides opportunities for frequent experimenting.
B.2.3.6. Examples NEC in practice
B.2.3.6.1. Optimal use of information
111. The maritime dimension traditionally has a strong multinational orientation. Individual units must be interoperable to be able to function in a multinational flotilla. A recent example (late 2005 - early 2006) was the Dutch contribution to Task Force 150, which was responsible for so-called maritime security operations in an area stretching from the coast of Somalia to the Arabian Gulf. TF 150 consisted of a great variety of navy vessels (including an air defence and command frigate), maritime patrol vessels, unmanned aircraft and shipborne helicopters. All these means contributed to the joint mission: identifying and detecting suspect vessels, boarding and searching vessels, collecting information and halting suspect vessels and arresting their crew. Through use of the American CENTRIX network and the Coalition Forces Intelligence Cell, the vessels could exchange information (such as photographs) with each other and with shore authorities directly by e-mail and chat, thus ensuring that the waiting time for merchant ships could be reduced to a minimum.
B.2.3.6.2. ISIS
112. Task Force Fox was a NATO force that was intended to protect the international observers who were tasked with monitoring the implementation of the peace plan for Macedonia in 2001-2002. In this multinational coalition with Germans, Frenchmen and Italians under Dutch leadership, the language barrier was, considering the operational circumstances, a real problem. Because information was shared with the coalition partners using ISIS, and this information was also represented graphically, there would soon be a shared understanding of the operational situation and emerging crises could be overcome swiftly and effectively. It is also thanks to ISIS that Task Force Fox has gone down in history as a successful NATO mission.
B.2.4. Spain
B.2.4.1. Policy and Direction
113. National policies and directives support the bringing in of the NEC model nationally as they do its contribution to the multinational efforts. Both, information superiority and interoperability are considered a force multiplier/booster at the Spanish Military Strategy. The National Defence Act speaks of a call to "urge a transformation of our Armed Forces in line with a new model which would give them advanced technological capabilities". The Organic Law of National Defence and the Military Planning Directive requires that "Armed Forces are to be organized and trained in such an advanced technological manner that they will thus enjoy combat advantage, fewer losses and less damage and be networking operative"
114. Aware of the very high number of actors and lines of work involved on Spanish NEC, in order to assure the proper co-ordination, CHOD set up a NEC Study and Developing Board (CEDENEC). This commission comes under the Chief of the Joint Staff responsibilities and is presided over by the Head of the CIS Division drawing its members from Defence staff HQ Spain and the HQs of each of the Services along with the Materiel and Armaments Board (DGAM), the CIS Inspectorate (IGECIS) and the Policy Board (DIGENPOL).
115. This organization gives the specific structure set up for the improving of the initiatives coherence that bring in other pertinent bodies, and for the generating proposals including those approaches required to make of Spanish NEC a reality and its contribution to NATO NEC a fact. This working whole structure, that includes a working groups subestructure and is supported by the Spanish NEC Office, is charged with giving leadership to NEC during its initial phases by answering questions as to its definition, objectives, requirements, criteria as to its functional structure, information infrastructure, interoperability and any other matter that might have an effect on the development of NEC. It is also to promote the NEC knowledge within the Spanish Armed Forces, specially to all the involved bodies in its definition and development and to manage NEC related information.
B.2.4.2. Shaping up Spanish NEC
B.2.4.2.1. Pre-emption: Strategic Framework and Complexity Management
116. Spain is aware that there is no single sequence of long-term planned baselines, but an approximate direction of progress, frequently reviewed and adapted to changing technologies, requirements and constraints. Therefore, CEDENEC believes that the best planning strategies under a high level of uncertainty and risk are no longer those that deliver optimum results in the very specific circumstances anticipated, but those that are robust enough to perform acceptably in a variety of potential scenarios. As such a strategic framework to answer the what-for, the what, the how and the when of the undertaking should be and should allow a balance among stability and flexibility.
117. The Spanish NEC Strategic Framework is under CEDENEC's development and covers what Spain must achieve in order to fulfil the operational requirements; Lays down the strategic lines of work including those related with conceptual development, methodology and best practices, design and implementation and shared awareness; Establishes the global plans which include the strategic lines of work and; Goes into details as to short term plans. As it is to be the case for any rolling strategy, operational and technical analysis and studies (including those lessons learned) are to be continuously improving upon this strategic framework. Last but not least in importance is the human dimension including morale, leadership, training, education and, doctrine. The strategic framework is also aimed to this aspects.
118. This strategic framework is to be considered within the Spanish Military Planning Process as well as within those efforts made of Defence bodies having technical responsibilities, research and development competences along with acquisitions responsibilities. In this situation the efforts towards the rolling orientation of running capabilities, programs and initiatives are going to be more important than ever.
B.2.4.2.2. Operational and Technical Interoperability Awareness
119. It is more important than ever to keep alive the operational and technical interoperability awareness that Spain has held essential for so many years and backed by her participating in different demonstrations, exercises and experiments.
120. It is to note Spanish technical experimentation at CWID initiatives. Spanish industry, universities and military bodies with technical competences play a part in the CWID demonstration. A Pilot model for SOA interoperability services, the Spanish Military Messaging System, Spanish web map services and web feature services or COP services have been put to work within latest NATO CWID. As it happened to be within other nations, Spain has its own national CWID. As such, middleware for sensors at C2 networks, or broad band mobile communications for tactical deployments, or tactical mini terminals for satellite band X communications have also been given demonstration airings.
121. Spain is also working on supporting infrastructures for experimentation, training and exercises. Noteworthy here is that Spain is working towards the setting up of a Laboratory for NEC experiments (CENEC) where any practical solutions put forward are to be measured against those operative demands. Advanced joint simulation facilities are to be keep financed next year. NEC related prototypes have been delivered to our Operational Post Command.
122. Following the NATO approach the development of our systems is in keeping with NC3TAv7 and NAFv2. Spain is analyzing its architectures views evolution in keeping with NAFv3 and NISP.
B.2.4.2.3. Follow-on
123. The main effort within the short to medium term must be towards achieving the Spanish NEC strategy for the managing of this complex endeavour and its concomitant experimental support demands.
124. In the medium to long term Spain expects to be able to have the run of a fully operative working whole structure, this taking into its scope civilian organizations and other ministries.
125. If there were something that could be called an international net-ready certification Spain could be deeply involved in it. Systems processes, capabilities and even acquisitions programmes could be verified on the basis of net-ready criteria or, to put it in another way: systems, processes, capabilities and acquisition programmes associated with network enabled capabilities could have what it might be call a "net-ready stamping". An interoperability authenticity stamp which would be, but of course, anchored upon the international determination it is concerned with. Which all means that an evaluation of existing systems will be called for to check out whether the net-ready criteria have been satisfied be it nationally or within any given coalition.
126. The Spanish acquisition process is aligned with NATO Phased Armaments Programming System (PAPS). This process came up for review under a new proposal. Among other aspects, it's under consideration a set of criteria that allows PAPS documents go further in the process, in order to enable rationalization as well as the necessary evolution in aspects such as technology.
127. Spain's ultimate vision is of a real federation of military and civilian services and its cross utilization for crisis management and current operations. Civilian and military bodies would natuarally provide any that were to be needed, services that would thus endow us with powerful dual capabilities for defence and security.
B.2.4.3. Implementation of the Spanish Core NII: The Spanish Military Command and Control System (SMCM)
128. In order to solve the interoperability and information flow problems caused by a fragmentary approach, the solution adopted is to define and implement a new C2 system, the SMCM (Joint C2 system), which will become the basic CIS infrastructure on which the specific services will be built. Of course this new system integrates the military telecommunications that have been integrated in a single joint system for many years (the Military Telecomunication System - STM) and is designed from the beginning to solve the shortfalls and problems of the existing information capabilities.
129. Its Military Information System (SIM) incremental process has been divided into 3 increments and a previous definition phase. In this definition phase, it has been developed and approved the Concept of Operation of the System, the System Planning and Funding. The first increment objective is to implement and provide a set of common services, like both PKI and Directory Services and the priority services like Military Messaging System. The system is to be deployed in the principal nodes (Joint, Land, Air and Maritime Headquarters, etc.) and is to be accredited to manage information upon National SECRET, NATO CONFIDENTIAL and CONFIDENTIAL UE level. The second increment includes the implementation of the specific functional services, the accreditation to NATO SECRET and SECRET UE, and it is planned to deploy the system to 400 nodes approximately. The last increment it is planned to provide all the functional area services and evolve the system to comply with the Network Enabled Capability. Of course, our will to set up this increments as schedule is tied to the available budgeting and funding.
B.2.4.4. POC
130. ESPNEC@oc.mde.es
B.2.5. Sweden
131. Authors:
-
Peder Blomqvist, Swedish Defence Material Administration
B.2.5.1. The Swedish Network Based Defence (NBD) concept
132. The Swedish Armed Forces has adopted the concept of Network Based Defence (NBD) as its main strategy to achieve Network Ready Capabilities. NBD is also the method for Swedish force transformation to Joint Operations and Capabilities and thus a fast, flexible and co-ordinated deployment of Reaction Force Units within national boundaries as well as a partner in an international mission. The NBD concept is the Swedish approach to retain the benefit of the Revolution in Military Affairs (RMA) and is similar to the Network Enabled Capabilities (NEC) and the Net-Centric Operations Warfare (NCOW) concepts.
B.2.5.2. Development of a Command and Control System within the NBD concept
133. The Swedish Armed Forces has within the concept of NBD since 2001 been developing frameworks, concepts, principles, rules and recommendations, as enablers and guidance for design, construction and operation of the methods, services and technology solutions that should form the foundations and infrastructure of a future Command and Control System. The goal is to deploy the target architecture and infrastructure of the C2-system within the year of 2010. The C2-system is being developed with interoperability and the usage of open standards and commercial products (COTS) in focus. Gradually the C2-system infrastructure will develop into a full-featured Net-centric C4ISTAR-system with incorporated functionality for other legacy systems as well as new systems.
134. The Swedish Armed Forces has during 2006 established a NBD Development Centre under the command of Chief of Development.
135. Sweden has adopted a Concept Development and Experimentation (CD&E) process based on international examples. One of the purposes of this process is to guarantee or secure interoperability.
136. Sweden has conducted experiments in three different military command levels and also in Multi-National Experimentation (MNE) events.
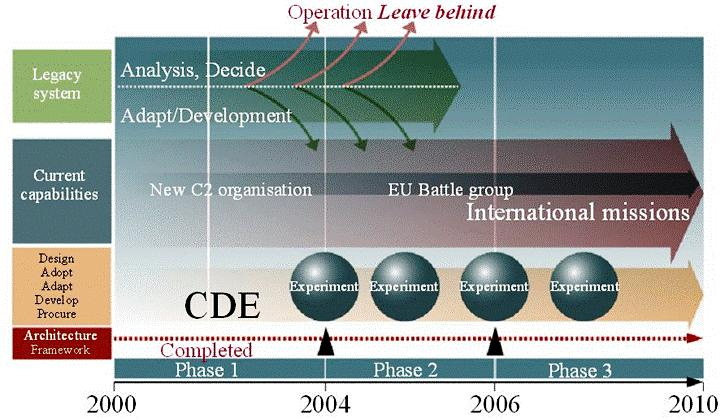
Figure B.8. Transformation Roadmap
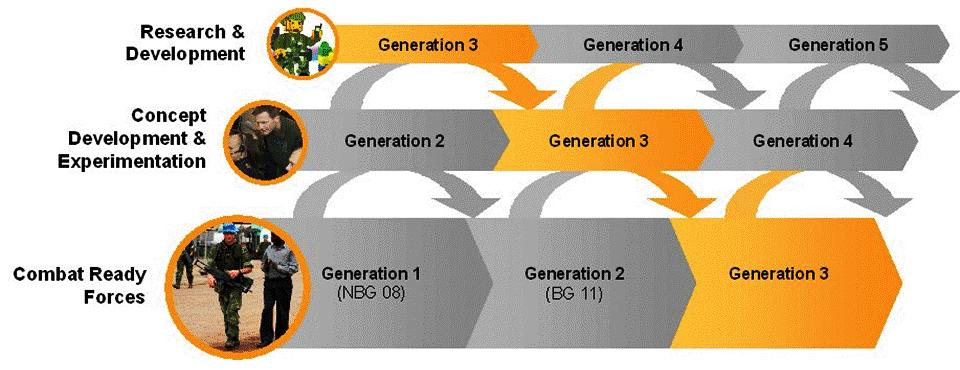
Figure B.9. CD&E Model
B.2.5.3. Development Strategy and Methodology
137. The development is a joint effort between the Swedish Armed Forces, the Swedish Defence Materiel Administration (FMV), the Swedish Defence Research Agency (FOI), the National Defence College (FHS), the industry and other partners. The development is based on an overarching architecture approach with concepts and principles for System, Services, Information and Life-Cycle management. The development strategy is to use an evolutionary development methodology with continuous and parallel research and development of methods, knowledge, organisation and technology. The results are tested, verified and validated in experiments and demonstrators, and then carefully packaged in form of generic principles, design rules and methods. These will gradually build up the target architecture with re-usable foundations and reference architectures for further development of service-oriented systems and components for net-centric environments. The Swedish Armed Forces development of the NBD joint Command and Control Information System (SWECCIS) results in the knowledge and erudition of building NBD operational systems.
B.2.5.4. Development Milestones for the Command and Control System 2004-2010
138. Autumn 2004: New development opportunities
139. Autumn 2005: Common situational information
140. Spring 2006: Common situational awareness
141. Autumn 2006: New opportunities for co-ordination
142. 2007-2010: Final design and procurement of the Command and Control System Information Infrastructure[6]
B.2.5.5. Interoperability
143. In autumn 2004 Sweden made a strategic decision to adopt current NATO standards and frameworks for C3-systems interoperability and to participate in and contribute to NATO's development of NNEC-based standards and frameworks, where possible as a partner nation. Lessons learned from the adoption of NATO standards and open standards and solutions create an environment that increases interoperability among crisis management agencies.
B.2.5.6. Main objectives of the Network Based Defence (NBD)
144. Interoperability - Ability to act in Joint Operations together with national and international partners, both military and civil. This can be achieved through standardisation and harmonisation of concepts, procedures and architecture.
145. Situation Adaptiveness - Flexible configuration and management of units, for given tasks and new opportunities. Dynamical configuration of Situation Adopted Systems, from a Baseline Architecture of resources and services. Well defined suites of Capability Packages for different scenarios.
146. Common Situational Awareness - Common Situational Information adopted for each user needs. Role-based situation picture and information access. Location and terminal independent distribution of data. Automated as well as on-demand collection, aggregation, fusion, processing, analysis, predictions and presentation of data and information from multiple sources.
147. Command Superiority - Swedish NBD experiment has showed that information that are fast distributed through out the Network and not compiled in centralised nodes empowers the lower echelon's to seize opportunities according to commander's intent as they come along.
148. Cost effectiveness - Flexible configuration will give us the ability to reuse and reconfigure systems and services in minutes instead of months/years. This together with the ability to bring along legacy systems should mean that the risk of building systems that are obsolete when operational also reduces the risk of wrongly spent money.
149. Precision Engagement - Co-ordinated and well balanced engagement, precise in time and location. This can be achieved by obtaining decision superiority.
B.2.5.7. The Service Demonstrator
150. The Swedish Defence Architecture project together with FM Ledsyst developed a set of concepts that supports a Service Based Systems approach where services can be assembled on demand into SitSyst, Situation adapted systems. A SitSyst is dedicated to solve a particular problem area or support a specific mission. These ideas and concepts were implemented during 2003 in a platform called The Service Demonstrator. The Service Demonstrator is a test system developed within Ledsyst in order to support the development towards a network centric defence. The purpose of the demonstrator is primarily to support the methodology development for network centric warfare.
151. The Service Demonstrator have continuously been updated and improved up until now. More system elements have been added and improvements have been made concerning stability, user functionality, application integration etc. Central concepts for The Service Demonstrator are SitSyst, dynamic addition and removal of services, creation of roles and authorization for solving specific tasks.
152. Built on experiences from the Service Demonstrator and lessons learned the development of a more extensive service based system, BasePlatform , began in 2005. The current version of BasePlatform specifies a platform design that addresses core functionality such as service infrastructure, security, scalability, flexibility etc.
B.2.5.8. FMA- An Enterprise Architecture for Future Systems in the Swedish Armed Forces
153. SAF Enterprise Architecture (FMA) for the 21st century is under development. Swedish Armed Forces needs to co-ordinate and synchronise different resources (personnel, technology and information) enabling them to perform right activity, in right time frame and in right area. These resources are co-ordinated and synchronised within an organisation. To synchronise all these mutual dependent systems and their development over time is the complex challenge that Swedish Armed Forces Enterprise Architecture shall support Swedish Armed Forces to master. The purpose of FMA is to obtain tools for enabling interoperability in co-operation with society in general and international co-operation partners as well. Another important aspect is to give conditions for re-use of resources within the frame of NBD. SAF engagement systems must therefore be developed against a harmonisation and towards one common structure of present and new structures. This development shall be supported through supplying an Architecture Framework (FM AR) containing overarching rules for:
-
How to describe a system
-
Methods for build and use systems
-
Competencies/roles in these systems
B.2.5.9. National NNEC Approaches
154. Some Swedish examples of key strategic programmes project experiences, products and best practice, lessons learnt, that can perhaps be of interest for the NATO and PfP nations.
-
FM LedsystT FMLS2010 Network Based Defence experiences
-
Documentation experiences (SwAF Architecture Framework, NAF v2)
-
SOA implementation experiences and best practice
-
Service Demonstrator experiences and best practice
-
NBD concepts, definitions and best practice
-
System concept
-
Service concept
-
Situation Adopted System concept (SitSyst)
-
Information concept
-
Life-cycle management concept
-
-
NBD Systems Development methodology work and
-
-
SwAF Enterprise Architecture development and NATO NAF 3 adjustment effort.
-
FM AR Concepts and models
-
NAF v2 and NAF v3 (pragmatic approach) documentation experiences and best practice
-
-
SWECCIS Reference Architecture experiences (Swedish Command and Control Information System), target architecture for SWECCIS 2008.
-
NAF v3 (pragmatic approach), documentation experiences and best practice
-
-
The SwAF ERP project (PRIO) and the service oriented requirement specification work.
B.2.6. The UK Network Enabled Capability
155. The UK has adopted the term Network Enabled Capability (NEC) as it captures it's intent to invest in networks as a means of maximizing the capability inherent in current and future platforms. The UK is using the term "Network Enabled Capability" since it gives due weight to both the platform capability and the network, and is consonant with their work on Effects Based Operations, Knowledge superiority and Decision Superiority.
156. The NEC goal is to radically enhance our operational capability by improving the way we share and use information , with the key objective of providing a coherent conceptual and technical framework to link sensors, decision-makers and effectors.
157. The US concept of Network Centric Warfare, put into practice in Afghanistan, is a key driver. In the same way that precision guided munitions demonstrated in the Gulf war acted as a driver for change in UK and other forces, the success of the US' strategy, implement through a tight linkage between sensors, communications, information, and weapons systems is causing the UK to look at how it would fight the next conflict.
158. Lessons learned have emphasized the importance of interoperability in the joint and coalition environment.
159. It is important to understand that the path to NEC is an evolutionary one that builds on existing equipment programmes, concepts and structures but delivers increased joint capability. The parallel evolution of the other UK Lines development (Concept & Doctrine, Structure, Equipment & Technology, People, Training, Sustainment) is an essential part of the progress towards a full Defence capability Existing processes will provide the links.
160. The diagram below shows the underlying principles in the UK in building its NEC.
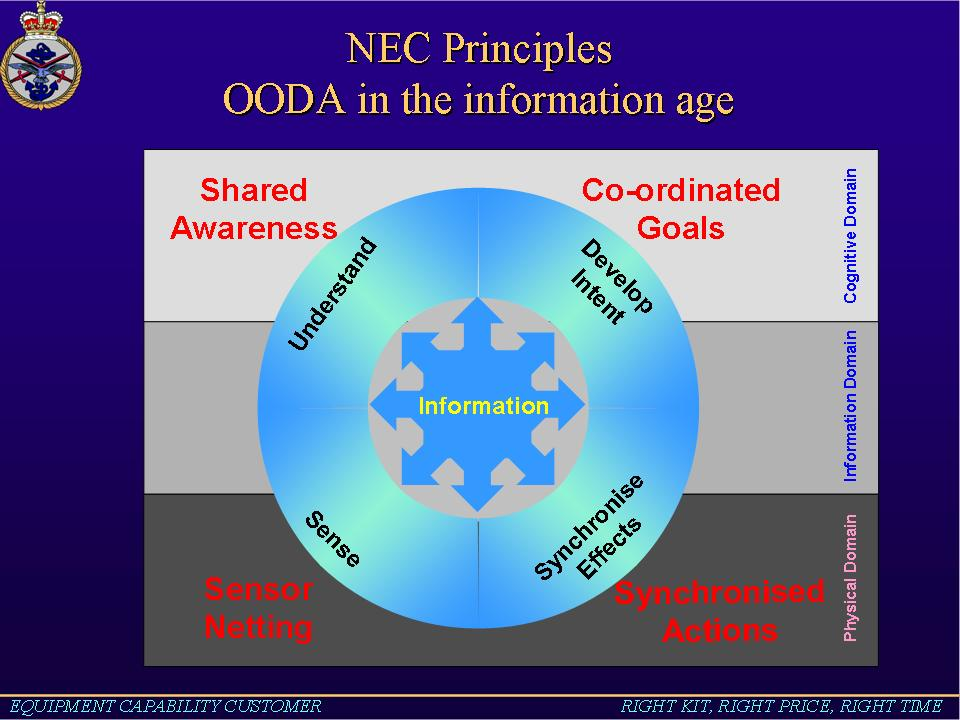
Figure B.10. NEC Themes
161. The table below summaries the key themes of the UK's NEC
| Effects Synchronization | Achieving the desired effects through the synchronisation of activities within and between mission groups. |
| Agile Mission Groups | Enabling the dynamic creation and configuration of task oriented mission groups that share understanding and that employ and co-ordinate available assets to deliver the desired effect. |
| Dynamic Collaborative Interworking | Enabling agile command and control within and between mission groups through the ability to concurrently plan and execute operations in a way that is dynamic, continuous and synchronised. Thus, it allows all entities (including non-frontline MoD bodies, Other Government Departments, industry, academia and public services as well as the military) to work together dynamically to meet changing mission needs. |
| Shared Understanding | Enabling each user to generate an understanding of the battlespace that is appropriate and adequate to their task and consistent with the understanding of other users. This understanding covers the interpretation of the situation (current situation, its history, and potential developments of all battlespace participants) and of Command Intent (the effects and outcomes higher command wants to achieve. |
| Full Information Accessibility | Enabling users to search, manipulate and exchange relevant information of different classifications (respecting security constraints) captured by, or available in, sources internal and external to the battlespace. |
| Resilient Information Infrastructure | Enabling information is managed coherently across the battlespace and that the potential for secure and assured connectivity is provided to all battlespace users. |
| Inclusive Flexible Acquisition | Co-ordinating processes across MOD, OGDs and industry that promotes the rapid insertion of new technologies, facilitates coherence between acquisition programmes and provides an incremental approach to delivering and sustaining 'net-ready platforms' |
Table B.1. UK NEC Themes
162. Further information can be found at: http://www.mod.uk/DefenceInternet/AboutDefence/CorporatePublications/ScienceandTechnologyPublications/NEC/
B.2.7. United States
B.2.7.1. Overview
163. The United States' Department of Defense (DOD) pioneering theory of Net-Centric Operations and Warfare (NCOW) has fundamentally changed how the United States plans for and engages in military operations. NCOW seeks to translate an information advantage into a competitive war-fighting advantage through the robust networking of well informed geographically dispersed forces allowing new forms of organizational behavior. This "networking" utilizes information technology via a robust network to allow increased information sharing, collaboration, and shared situational awareness, which theoretically allows greater self-synchronization, speed of command, and mission effectiveness.
B.2.7.2. Net Centric Efforts
B.2.7.2.1. The Global Information Grid (GIG) Bandwidth Expansion Program
164. The Global Information Grid Bandwidth Expansion (GIG-BE) Program was a major Department of Defense (DOD) net-centric transformational initiative executed by DISA. GIG-BE created a ubiquitous "bandwidth-available" environment to improve national security intelligence, surveillance and reconnaissance, information assurance, as well as command and control. Through GIG-BE, DISA leveraged DOD's existing end-to-end information transport capabilities, significantly expanding capacity and reliability to locations worldwide.
165. This program provided increased bandwidth and diverse physical access to approximately 87 critical sites in the continental United States (CONUS), Pacific Theater, and European Theater. These locations are interconnected via an expanded GIG core.
166. GIG-BE provides a secure, robust, optical terrestrial network that delivers very high-speed classified and unclassified Internet Protocol (IP) services to key operating locations worldwide.
167. After extensive component integration and operational testing, implementation began in the middle of the 2004 fiscal year and extended through calendar year 2005. The initial implementation concentrated on six sites used during the proof of initial operational capability, achieved on Sept. 30, 2004. On Dec. 20, 2005, the GIG-BE program achieved the milestone of Full Operational Capability.
B.2.7.2.2. Transformational Communications Satellite System (TSAT)
168. The TSAT Program is actually just one node in a broad spectrum of programs known as the Transformational Communications Architecture (TCA). In 2001, the United States Department of Defense (DOD) initiated a Transformational Communications Study to accelerate the delivery of advanced capabilities with state-of-the art technology to the field.
169. The study concluded that the United States Military's existing program plan would not meet forecast communications requirements. It also suggested that there was a window of opportunity to provide an architectural framework for a compatible communications system across the Department of Defense and the intelligence community - one that could increase U.S. capabilities by a factor of ten.
170. Those conclusions, plus ongoing experience in the Global War on Terror and new technology developments like UAVs, helped shape the Transformational Communications Architecture (TCA).
171. TSAT is intended to provide internet-like capability that extends high-bandwidth satellite capabilities to deployed troops worldwide, and delivers an order of magnitude increase in available military bandwidth. Using laser communications inter-satellite links to create a high data-rate backbone in space, TSAT will be one of the key enablers for the American vision of Network Centric Warfare.
172. A visual image from a UAV that would take 2 minutes to process with the Milstar II satellite system would take less than a second with TSAT. A radar image from a Global Hawk UAV (12 minutes), or a multi-gigabyte radar image from space-based radar (88 minutes), would also take less than a second with the TSAT network. Best of all, the recipient can be on the move with a relatively small receiver, anywhere in the world.
173. The TSAT system is currently scheduled to launch in 2013-2016.
B.2.7.2.3. Wide-Band Satellite Communications
174. Wide-Band Satellite communications provides ubiquitous communications with optical quality bandwidth to mobile and tactical users.
175. The Wideband Gapfiller Satellite program and the Advanced Wideband System will augment and eventually replace the Defense Satellite Communications System (DSCS) in 2009 or 2010. These satellites will transmit several gigabits of data per second-up to ten times the data flow of the satellites being replaced.
176. Protected communications will be addressed by a global extremely high frequency (EHF) system, composed of the Advanced Extremely High Frequency System and Advanced Polar System. These systems are expected to provide about ten times the capacity of current protected satellites (the Milstar satellites). Narrowband needs are supported by the UFO (Ultrahigh-frequency Follow-On) constellation, which will be replaced by a component of the Advanced Narrowband System.
177. Capacity gains in these systems will also be matched by improved features, such as multiple high-gain spot beams that are particularly important for small terminal and mobile users. Satellite, terminal, control, and planning segments will utilize emerging technology to ensure the best capability for the cost. Coordination among ground, air, and space segments and between government and commercial assets will help ensure deployment of the most efficient, effective, and affordable communications systems.
B.2.7.2.4. Net-Centric Enterprise Services
178. Net-Centric Enterprise Services (NCES) is a Department of Defense program, managed by the Defense Information Systems Agency (DISA), to develop information technology infrastructure services for future systems used by the United States military to support the broad range of applications and data used in a net-centric enterprise. There are nine core enterprise services defined in the Network Centric Operations and Warfare - Reference Model (NCOW-RM):
-
Storage
-
Mediation
-
User Assist
-
IA (Information Assurance)
-
ESM (Enterprise Service Management)
-
Messaging
-
Discovery
-
Application
-
Collaboration
179. NCES maps these nine services to four product areas:
-
Enterprise Service Oriented Architecture (SOA) Foundation
-
Content Discovery & Delivery
-
Enterprise Collaboration
-
Defense On-Line Portal
B.2.7.2.5. Horizontal Fusion
180. Horizontal Fusion (HF) program refers to the net-centric applications and content needed to provide analysts and war fighters with the ability to make sense of complex and ambiguous situations. Within HF, the first implementation of a Service Oriented Architecture (SOA) in the Department of Defense was achieved. The demonstration proved that the realization of a Net-Centric environment is technically feasible using legacy investments. Horizontal fusion is not just a single program, but a portfolio of net-centric initiatives using a common architecture and integration process. Recent initiatives include the following:
-
Department of State: Net-Centric Diplomacy . Net-Centric Diplomacy is an initiative aimed at enhancing war fighters' ability to gain situational understanding about adversaries and their operating environment by providing a full range of diplomatic reporting from worldwide posts to the collateral space, provided upon demand via net-centric DOD information services accessible through the MARS portal.
-
Environment Visualization (EVIS) . EVIS produces forecasted weather effects on tactical missions and makes these available and advertised through the enterprise, enabling a user to access high resolution, mission-tailored weather effects summaries and related map overlays, and do this within their tactical decision-making cycle.
-
Information Assurance / Certification and Accreditation Process . IA/CA will provide streamlined certification and accreditation services; makes recommendations and advocates for policy changes to support the certification and accreditation of net-centric operations.
-
Joint Surveillance Target Attack Radar System (Joint STARS)/ Affordable Moving Surface Target Engagement (AMSTE) . Joint STARS/AMSTE brings a sophisticated moving-object tracking capability to Horizontal Fusion that enables tracking more targets with greater accuracy. Joint STARS/AMSTE can push these tracks to a ground station using either a line of sight or beyond line of sight data link, with the ground station converting both the moving target indicator reports and tracks into an XML message and sending it to the MAJIIC initiative for publication.
-
Knowledge Management in a Net-Centric Environment (KMINCE) . Based on the National Ground Intelligence Center's mission, KMINCE provides tactical data, intelligence reports, publishing/posting tools, and collaboration functions within a web-accessible, service oriented environment. KMINCE allows operational users to search tactical databases through a Federated Search interface, build and post intelligence products within the collateral space and collaborate within the Horizontal Fusion MARS portal.
-
Multi-Sensor Aerospace-Ground Joint ISR Interoperability Coalition (MAJIIC) . MAJIIC enhances U.S. joint and coalition ISR data interoperability and MAJIIC enhances information sharing via the development, testing, and implementation of data standards, XML schemas, and leading edge Web-based enterprise services. MAJIIC will "post-before-processing" to the collateral space U.S. and coalition near-real-time ISR sensor data and mission situational awareness information for discovery and smart-pull by Mars Portal users and value-adding command, control, communications, computers (C4), ISR systems.
-
Net-Centric Geospatial-Intelligence Services (NGS) . NGS is a portlet on the Mars portal that provides the nation's war fighters and senior policymakers with access to geospatial intelligence (GEOINT), the exploitation and analysis of imagery and geospatial information to describe, assess and visually depict physical features and geographically referenced activities on Earth.
-
Network Basic Language Translation Services (NetBLTS) . Network Basic Language Translation System (NetBLTS) enables non-linguists to quickly triage foreign documents and provides a translation aid to linguists. NetBLTS provides Optical Character Recognition (OCR), machine translation, and document management and indexing. Users can save extracted keywords and phrases, document translations, and foreign documents to a database repository for future analysis. The repository is accessible through the Horizontal Fusion Federated Search application.
-
Non-Obvious Relationship Awareness (NORA) . NORA discovers relationships among people and organizations to answer the question, "Who knows whom?" and can be accessed by the war fighter through the Mars Portal and collateral space.
-
Trusted Wisdom . Trusted Wisdom provides secure, mobile, real-time posting of reporting from field collectors. Information is tagged and accessible in the collateral space, where communities of interest can host rapid analysis and fusion of field collector reporting and technical collection data, and serve as venue for field collector, analyst, and war fighters to interact and rapidly develop fused actionable intelligence.
-
Visual Enterprise Monitoring (VEM) . VEM provides a "window to the information flow" within a network to increase commanders' and decision-makers' overall situational awareness.
-
Visualization/Information Dominance (V/ID) . V/ID bridges traditionally separate analytic processes, including data preparation and exploitation, and Web-enables it through data extraction, analysis and tagging, via the commercial ClearForest ClearTags entity extractor. Visualization capability is enhanced/enabled using the commercial Starlight toolkit.
-
Coalition Shared Intelligence Networked Environment (COSINE) . COSINE combines analysis/production-sharing and cross-coalition information management married to a CENTRIXS -like secure network structure for intelligence exchange and content-based information security and release management capabilities that will allow individual coalition domains to quickly connect secure coalition command, control, and intelligence systems, share information and coordinate with both allied and coalition partners in a timely (near real-time) secure manner, and dynamically alter access to information when the need arises.
-
Cooperative Engagement Capability (CEC) . CEC webTracks initiative provides access to the CEC sensor network's real-time air track picture and make it accessible to a variety of clients via intelligent pull to allow tailoring of the data requested for either current or historical track data and underlying measurement data, or streaming data to constantly update track movements.
-
Extensible Tactical C4I Framework (XTCF) . XTCF is an open, extensible, plug-and-play architecture that will transform command and control data management services by providing an architecture that will rapidly add new value-added services and get new content providers and consumers quickly onto the collateral space in a dynamic battle space.
-
Global Net-Centric Surveillance and Targeting (GNCST) . GNCST is developing a capability to demonstrate model-based fusion of upstream data from multiple intelligence sources to detect, locate and identify time-critical targets and targets of national interest, and to distribute target reports to tactical users via collateral networks in tactically relevant timelines.
-
Integration of Non-Traditional Information Sources (INTIS) . INTIS uses non-traditional sensors, the F/A-18 Hornet and the AH-64 Apache, to provide secure, rapid delivery of hostile surface-to-air missile and anti-aircraft electronic intelligence to the war fighter and the intelligence community, aiding in fast updates of the common operating picture and more accurate targeting information.
-
Naval Research Lab (NRL) Sensor Node . Provides an airborne node on the collateral space for target location and detection to support ground troops and joint strike forces directly, by posting "sensor products" (e.g., imagery, data, reports) and alerts for immediate use in operational planning by various Web-enabled users.
-
Ocean Surveillance Information System Evolutionary Development (OED) . As the only operational command, control, communications, computer, and intelligence system trusted to provide multi-level secure capability, OED supports the customers of US and partner Joint Intelligence Centers with information tailored to their clearance level, area of interest, and need to know.
-
Secure Mobile Networks . Provides the war-fighter with secure, robust voice and data communication networks which enable collaboration even in highly dynamic, unpredictable, mobile wireless environments. Secure Mobile Networks are intelligent, resilient, and self-configuring networks that allow access to global assets in the field even when direct links with reach back communications are not available.
-
Trusted Workstation (TWS) . TWS provides intelligence analysts and operational war fighters with on-demand simultaneous access to common and mission-critical desktop applications running at multiple security domains from a single ultra-thin-client workstation.
-
Ubiquitous Automated Information Manager (U-AIM) . U-AIM enables the aiming of external information resources to automatically discover, access, associate, and prioritize intelligence and information products, and focus and allocate resources on high priority information needs through a simple Web application that allows the war fighter to continuously formulate target or event nomination and receive alerts, all tailored to the war fighter's role and mission.
-
Warrior's Edge . The Army's Warrior's Edge represents a dynamic ad hoc networked local sensing environment comprising soldiers and unattended and robotic sensors, each providing a user-tailored perspective of the combat situation to the war fighter during changing conditions to maximize mission success.