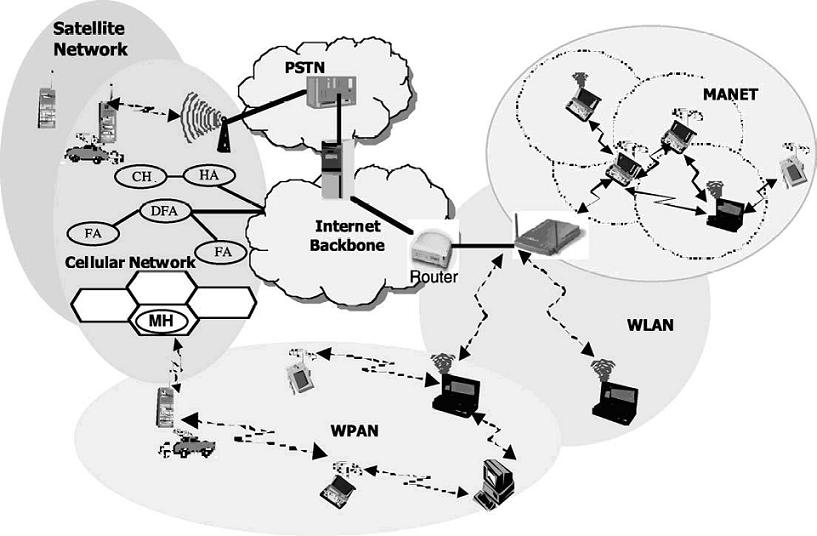
2.8. Networking
2.8.1. Mobile Ad-hoc Network (MANET)
171. MANET can be set up to connect military groups that need to maintain communications while on the move. Wireless sensor networks, on the other hand, are stationary. They are often deployed in areas hostile to humans and relay on a variety of observational data that are passed onto military personnel stationed at safer vantage points.
172. The potential integration of these two network types can provide the cornerstone of a truly 'network-centric' communications infrastructure. However, in order for NATO to fully utilize wireless technology, future technology should be focused on addressing the current deficiencies in wireless technology. These include:
-
Improvements in extending wireless range capabilities
-
Increasing transfer rates
-
Technology that will create more resilient/reliable links
-
Evolving routing protocols to better secure wireless networks
-
Technology that will not only choose the best path for routing packets but will also choose the best frequency as well.
2.8.1.1. Ad Hoc On-Demand Distance Vector (AODV)
173. The Ad Hoc On-Demand Distance Vector routing protocol is intended for use by mobile nodes in an ad hoc network. It offers quick adaptation to dynamic link conditions, low processing and memory overhead, low network utilization, and establishment of both unicast and multicast routes between sources and destinations. It uses destination sequence numbers to ensure loop freedom at all times (even in the face of anomalous delivery of routing control messages), solving problems (such as ``counting to infinity'') associated with classical distance vector protocols.
174. Importance: Designed for ad hoc mobile networks and is capable of both unicast and multicast routing.
2.8.1.2. Dynamic Source Routing (DSR)
175. The Dynamic Source Routing (DSR) is a routing protocol for wireless mesh networks. It is similar to AODV in that it forms a route on-demand when a transmitting computer requests one. However, it uses source routing instead of relying on the routing table at each intermediate device.
176. Determining source routes requires accumulating the address of each device between the source and destination during route discovery. The accumulated path information is cached by nodes processing the route discovery packets. The learned paths are used to route packets. To accomplish source routing, the routed packets contain the address of each device the packet will traverse. This may result in high overhead for long paths or large addresses, like IPv6. To avoid using source routing, DSR optionally defines a flow id option that allows packets to be forwarded on a hop-by-hop basis.
177. This protocol is truly based on source routing whereby all the routing information is maintained (continually updated) at mobile nodes. It has only 2 major phases which are Route Discovery and Route Maintenance. Route Reply would only be generated if the message has reached the intended destination node (route record which is initially contained in Route Request would be inserted into the Route Reply).
178. To return the Route Reply, the destination node must have a route to the source node. If the route is in the Destination Node's route cache, the route would be used. Otherwise, the node will reverse the route based on the route record in the Route Reply message header (symmetric links). In the event of fatal transmission, the Route Maintenance Phase is initiated whereby the Route Error packets are generated at a node. The erroneous hop will be removed from the node's route cache; all routes containing the hop are truncated at that point. Again, the Route Discovery Phase is initiated to determine the most viable route.
179. Importance: The protocol allows multiple routes to any destination and allows each sender to select and control the routes used in routing its packets. Also allows for a very rapid recovery when routes in the network change.
180. Status: IETF DSR Draft- version 1.0 has had many successful implementations. One of which is the open source DSR-UU that can run on Linux. DSR-UU implements most of the basic DSR features specified in the DSR draft (version 10). One big exception is flow extensions.
2.8.2. Knowledge Based Networking
181. A Knowledge Based Network would make decisions about the wireless spectrum and have intelligent nodes that could automatically optimize the network. If a connection spans reliable and unreliable parts of a network, there could be performance issues: if a packet makes it through the reliable region but is dropped in the unreliable part, it would have to be resent through the entire connection. A Knowledge Based Network would automatically break this connection into two smaller connections, one across the reliable region and one across the unreliable region. Then, if data is lost across the unreliable part, it would only need to be re-sent along that region of the network. This technique could increase bandwidth tenfold.
182. Also, in a knowledge based network it would take note of frequently accessed data and save copies on the edge of the network for quick access: the idea is If one soldier needs a piece of map data, then the guys around him will need it too. Artificial intelligence could even decide which protocols to use.
183. Such an intelligent network would not only understand how to move data; it would also be able to understand what the data meant to users. This idea is based on this concept of the Semantic Web, which called for Web pages to include machine-readable data in addition to content intended to be read by people. Software agents would use this data to understand the meaning of documents instead of simply searching for keywords.