G.10. Core Enterprise Services
417. Core Enterprise Services (CES) provide generic, domain independent, technical functionality that enables or facilitates the operation and use of Information Technology (IT) resources. CES will be broken up further into:
-
Infrastructure Services (incl. Information Assurance (IA) services)
-
Service Oriented Architecture (SOA) Platform Services
-
Enterprise Support Services
G.10.1. Infrastructure Services
418. Infrastructure Services provide software resources required to host services in a distributed and federated environment. They include computing, storage and high-level networking capabilities.
| ID:Service/Purpose | Standard | Implementation Guidance |
|---|---|---|
| 1:Infrastructure Processing Services: Virtualized Processing Services | Recommended:
ISO/IEC 17203:2011, Information technology -- Open Virtualization Format (OVF) specification also published as ANSI standard INCITS 469-2010 (OVF 1.1.0) Emerging: Distributed Management Task Force - DSP0243 2.0.1 , Open Virtualization Format Specification (OVF 2.0.1), 30 Aug 2013 |
Using Open Virtualization Format, Option B Mission Participant can create single, pre-packaged appliances and Service providers can export and import virtual machines that can run across different virtualization platforms. |
| 2:Distributed Time Services: Time synchronization | Mandatory:
IETF RFC 5905: 2010, Network Time Protocol version 4 (NTPv4). Mission Network Contributing Participants must be able to provide a time server on their network element either directly connected to a stratum-0 device or over a network path to a stratum-1 time server of another Mission Network Contributing Participant. Other mission participants must use the time service of their host. |
A stratum-1 time server is directly linked (not over a network path) to a reliable source of UTC time (Universal Time Coordinate)
such as GPS, WWV, or CDMA transmissions through a modem connection, satellite, or radio.
Stratum-1 devices must implement IPv4 and IPv6 so that they can be used as timeservers for IPv4 and IPv6 Mission Network Elements. The W32Time service on all Windows Domain Controllers is synchronizing time through the Domain hierarchy (NT5DS type). |
| 3:Domain Name Services: Naming and Addressing on a FMN instance | Mandatory:
|
|
| 4:Identification and addressing of objects on the network. | Mandatory:
|
Namespaces within XML documents shall use unique URLs or URIs for the namespace designation. |
| 5:Infrastructure Storage Services: storing and accessing information about the time of events and transactions | Mandatory:
ISO/IEC 9075 (Parts 1 to-14):2011, Information technology - Database languages - SQL Databases shall stores date and time values everything in TIMESTAMP WITH TIME ZONE or TIMESTAMPTZ |
Missions might conduct transactions across different time zones. Timestamps are essential for auditing purposes. It is important that the integrity of timestamps is maintained across all Mission Network Elements. From Oracle 9i, PostgreSQL 7.3 and MS SQL Server 2008 onwards, the time zone can be stored with the time directly by using the TIMESTAMP WITH TIME ZONE (Oracle, PostgreSQL) or datetimeoffset (MS-SQL) data types. |
| 6:Infrastructure IA Services: Facilitate the access and authorization between FMN users and services. | Mandatory:
Directory access and management service:
|
Options available to FMN members when joining their network element to a FMN instance:
For cross application/service authentication between separate forests claims based authentication mechanisms (SAML 2.0 or WS-trust/WS-Authentication) shall be used. Whilst LDAP is a vendor independent standard, in practice Microsoft Active Directory (AD) is a common product providing directory services on national and NATO owned Mission Network elements. AD provides additional services aside from LDAP like functionality. |
| 7:Infrastructure IA Services: Digital Certificate Services | Mandatory:
ITU-T X.509 (11/2008), Information technology - Open systems interconnection - The Directory: Public-key and attribute certificate frameworks
NATO Public Key Infrastructure (NPKI) Certificate Policy (CertP) Rev2, AC/322D(2004)0024REV2 Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile – PKIX (IETF: RFC 5280, 2008) Recommended: X.509 Internet Public Key Infrastructure Online Certificate Status Protocol – OCSP (IET: RFC 6960, 2013) |
|
| 8:Infrastructure IA Services: Authentication Services | Mandatory:
IETF RFC 1510:1993, The Kerberos Network Authentication Service (V5). |
G.10.2. SOA Platform Services
419. SOA Platform Services provide a foundation to implement web-based services in a loosely coupled environment, where flexible and agile service orchestration is a requirement. They offer generic building blocks for SOA implementation (e.g. discovery, message busses, orchestration, information abstraction and access, etc.) and can be used as a capability integration platform in a heterogeneous service-provisioning ecosystem.
| ID:Service/Purpose | Standard | Implementation Guidance |
|---|---|---|
| Web Platform Services | Mandatory:
|
HTTP shall be used as the transport protocol for information without 'need-to-know' caveats between all service providers and consumers (unsecured HTTP traffic). HTTPS shall be used as the transport protocol between all service providers and consumers to ensure confidentiality requirements (secured HTTP traffic). Unsecured and secured HTTP traffic shall share the same port. |
| 2:Publishing information including text, multimedia, hyperlink features, scripting languages and style sheets on the network | Mandatory:
HyperText Markup Language (HTML) 4.01 (strict)
|
|
| 3:Providing a common style sheet language for describing presentation semantics (that is, the look and formatting) of documents written in markup languages like HTML. | Mandatory:
Cascading Style Sheets (CSS), Level 2 revision 1 (CSS 2.1), W3C Recommendation, September 2009. Emerging (2014): Cascading Style Sheets (CSS) Level 3:
|
|
| 4:General formatting of information for sharing or exchange. | Mandatory:
|
XML shall be used for data exchange to satisfy those IERs within a FMN instance that are not addressed by a specific information exchange standard. XML Schemas and namespaces are required for all XML documents. |
| 5:Providing web content or web feeds for syndication to web sites as well as directly to user agents. | Mandatory:
Recommended: (Really Simple Syndication) RSS 2.0 Specification Version 2.0.11, 30 March 2009. |
For backwards compatibility it is recommended to also implement RSS 2.0. |
| 6:Encoding of location as part of web feeds | GeoRSS: Geographically Encoded Objects for RSS feeds:
Mandatory:
GeoRSS Simple encoding for <georss:point>, <georss:line>, <georss:polygon>, <georss:box>. Recommended:GeoRSS GML Profile 1.0 a GML subset for <gml:Point>, <gml:LineString>, <gml:Polygon>, <gml:Envelope> of
|
GML allows you to specify a coordinate reference system (CRS) other than WGS84 decimal degrees (think lat/long). If there is a need to express geography in a CRS other than WGS84, it is recommended to specify the geographic object multiple times, one in WGS84 and the others in your other desired CRSes. Schema location for GeoRSS GML Profile 1.0: http://georss.org/xml/1.0/gmlgeorss.xsd |
| 7:Message Security for web services | Conditional: When classified data is processed.
Emerging (2015):
Recommended:
|
Specifies how integrity and confidentiality can be enforced on messages and allows the communication of various security token
formats, such as SAML, Kerberos, and X.509v3. Its main focus is the use of XML Signature and XML Encryption to provide end-to-end
security.
Specifies a process for encrypting data and representing the result in XML. Referenced by WS-Security specification. Specifies XML digital signature processing rules and syntax. Referenced by WS-Security specification. For Securing RESTful Services use the OAuth standard. Easier to implement than SAML Token Profile. Suitable for service to service interactions only. Guidance for properly labelling and binding data objects for transport using SOAP, JSON, etc. are provided in the emerging Technical and Implementation Standard for Confidentiality Labelling of NATO Information (AC/322-(2014)xxxx) |
| 8:Security token format | Mandatory:
|
Provides XML-based syntax to describe users security tokens containing assertions to pass information about a principal (usually
an end-user) between an identity provider and a web service.
Describes how to use SAML security tokens with WS-Security specification. |
| 9:Security token issuing | Mandatory:
|
Uses WS-Security base mechanisms and defines additional primitives and extensions for security token exchange to enable the
issuance and dissemination of credentials within different trust domains. Extends WS-Trust to allow federation of different
security realms.
Used to describe what aspects of the federation framework are required/supported by federation participants and that this information is used to determine the appropriate communication options. |
| 10:Transforming XML documents into other XML documents | XSL Transformations (XSLT) Version 2.0, W3C Recommendation 23 Jan 2007 | Developer best practice for the translation of XML based documents into other formats or schemas. |
| 11:Configuration management of structured data standards, service descriptions and other structured metadata. | ebXML v3.0: Electronic business XML Version 3.0, Registry Information Model
(ebRIM), OASIS Standard, 2 May 2005
Registry Services and Protocols (ebRS), OASIS Standard Universal Description, Discovery, and Integration Specification (UDDI v 3.0), OASIS Standard. |
Used as foundation for setup, maintenance and interaction with a (FMN) Metadata Registry and Repository for sharing and configuration management of XML metadata. Also enables federation among metadata registries/repositories. |
| 12:Exchanging structured information in a decentralized, distributed environment via web services | Mandatory:
Conditional: Representational State Transfer (REST) in accordance with: University of California, Roy Thomas Fielding, Architectural Styles and the Design of Network-based Software Architectures: 2000, Irvine, CA. Emerging (2014):
|
The preferred method for implementing web-services are SOAP, however, there are many use cases (mash-ups etc.) where a REST
based interface is easier to implement and sufficient to meet the IERs.
Restful services support HTTP caching, if the data the Web service returns is not altered frequently and not dynamic in nature. REST is particularly useful for restricted-profile devices such as mobile phones and tablets for which the overhead of additional parameters like headers and other SOAP elements are less. |
| 13:Secure exchange of data objects and documents across multiple security domains | Mandatory:
|
Guidance for properly labelling and binding data objects is provided in the emerging Technical and Implementation Standard for Confidentiality Labelling of NATO Information (AC/322-(2014)xxxx) |
| 14:Topic based publish / subscribe web services communication | WS-Notification 1.3 including:
|
Enable topic based subscriptions for web service notifications, with extensible filter mechanism and support for message brokers |
| 15:Providing transport-neutral mechanisms to address web services |
Mandatory:
Web Services Addressing 1.0 – Core, W3C Recommendation, 9 May 2006 |
Required for WS-Security |
| 16:Reliable messaging for web services | Recommended:
OASIS, Web Services Reliable Messaging (WS-Reliable Messaging) Version 1.2, OASIS Standard, February 2009. |
Describes a protocol that allows messages to be transferred reliably between nodes implementing this protocol in the presence of software component, system, or network failures. |
|
[a] This specification is subject to the following copyright: (c) 2001-2006 BEA Systems, Inc., BMC Software, CA, Inc., International Business Machines Corporation, Layer 7 Technologies, Microsoft Corporation, Inc., Novell, Inc. and VeriSign, Inc. All rights reserved. |
||
G.10.3. Enterprise Support Services
420. Enterprise Support Services are a set of Community Of Interest (COI) independent services that must be available to all members within a FMN instance. Enterprise Support Services facilitate other service and data providers on network elements by providing and managing underlying capabilities to facilitate collaboration and information management for end-users.
G.10.3.1. Unified Communication and Collaboration Services
421. Unified Communication and Collaboration Services provide users with a range of interoperable collaboration capabilities, based on standards that fulfill NATO and Coalition operational requirements. They will enable real-time situational updates to time-critical planning activities between coalition partners, communities of interest (e.g. the Intel community or the Logistics community), and other agencies. Levels of collaboration include awareness, shared information, coordination and joint product development.
422. Different use cases require different levels of protection of these communication and collaboration services. For voice or audio-based collaboration services, the FMN profile provides interoperability standards for three different scenarios:
-
Voice over IP (VoIP) network services
-
Voice over Secure IP (VoSIP) network services
-
Network agonistic Secure Voice Services (such as 3G, IP/4G, ISDN)
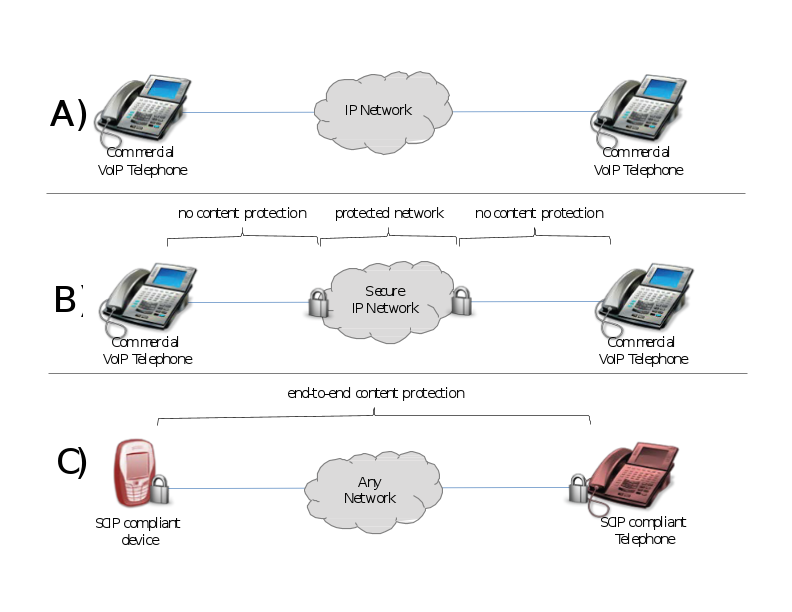
423. Depending on the security classification of a FMN instance, Scenario A or B are mandatory. If a member choses to use network agnostic Secure Voice services in addition to VoSIP, then SCIP specifications as defined for audio-based collaboration services (end-to-end protected voice) should be used.
424. For text-based collaboration there is also a basic profile sufficient for operating this service with reduced protection requirements as well as an enhanced XMPP profile that includes additional security mechanisms.
| ID:Service/Purpose | Standard | Implementation Guidance |
|---|---|---|
| 1:Video-based Collaboration Services (VTC) | Mandatory (VTCoIP):
|
|
| 2:Audio-based Collaboration Services | VoIP numbering:
STANAG 4705 Ed. 1 Ratification Draft, International Network Numbering for Communications Systems in use in NATO Mandatory (VoIP):
Emerging (2015):
|
VoIP refers to unprotected voice communication services running on unclassified IP networks e.g. conventional IP telephony
(see scenario A in Figure above)
VoSIP refers to non-protected voice service running on a classified IP networks (see scenario B in Figure above) Voice sampling Interval 40ms |
| 3:Audio-based Collaboration Services (end-to-end protected voice) | Conditional:
|
Secure voice services (see scenario C in Figure above)
V.150.1 support must be end-to-end supported by unclassified voice network SCIP-214 only applies to gateways Note that SCIP-216 requires universal implementation. |
| 4:Informal messaging services (e-mail) | Mandatory:
Emerging (2016): IETF RFC 5321: 2008, Simple Mail Transfer Protocol which obsoletes: IETF RFC 2821: 2001 IETF RFC 5321: 2008, Simple Mail Transfer Protocol which obsoletes IETF RFC 2821: 2001 Emerging (2017): IETF RFC 6477: 2012, Registration of Military Message Handling System (MMHS) Header Fields for Use in Internet Mail IETF RFC 6477: 2012, Registration of Military Message Handling System (MMHS) Header Fields for Use in Internet Mail |
Conditional: Depending on the protection requirements within the particular FMN instance messages must be marked in the message
header field “Keywords”(IETF RFC 2822) and first-line-of-text in the message body according to the following convention:
[MMM] [CLASSIFICATION], Releasable to [MISSION] Where CLASSIFICATION is the classification {SECRET, CONFIDENTIAL, RESTRICTED, UNCLASSIFIED} and MMM is the alpha-3 country code e.g. DEU, GBR, as defined in Table 8.ID2 with the exception that NATO will be identified by the four letter acronym “NATO”. The “releasable to” list shall include the short-name of the mission and may be extended to include other entities. Example: Keywords: ITA UNCLASSIFIED, Releasable to XFOR Conditional (if the mission network operates at classified level). messages must be labelled and bound to the email transport using the SMTP Binding Profile defined in Technical and Implementation Standard for Confidentiality Labelling of NATO Information (AC/322-(2014)xxxx |
| 5:Content encapsulation within bodies of internet messages | Multipurpose Internet Mail Extensions (MIME) specification:
|
10 MB max message size limit
Minimum Content-Transfer-Encoding:
Minimum set of media and content-types:
|
| 6:text-based collaboration services | Mandatory: basic FMN XMPP profile (see 6.1)
Recommended: enhanced FMN XMPP profile (see 6.2) |
Near-real time text-based group collaboration capability for time critical reporting and decision making in military operations. |
| 6.1:text-based collaboration services (basic FMN XMPP profile) | IETF RFC 6120: 2011, Extensible Messaging and Presence Protocol (XMPP): Core.
IETF RFC 6121: 2011, Extensible Messaging and Presence Protocol (XMPP): Instant Messaging and Presence. The following XMPP Extension Protocols (XEP) defined by the XMPP Standards Foundation shall also be supported:
Fading:
|
|
| 6.2:text-based collaboration services (enhanced FMN XMPP profile) | The enhanced profile requires compliance with the basic profile as defined above plus:
Emerging
|
Developers are also advised to consult the following IETF RFCs:
Many XMPP extensions are still in draft. Implementations should use caution i.e. XEP-0065: SOCKS5 Bytestreams, April 2011. XMPP Extension Label syntax should follow the emerging NATO standard: Technical and Implementation Standard for Confidentiality Labelling of NATO Information (AC/322 (2014)xxxx) |
G.10.3.2. Information Management Services
425. Information Management Services provide technical services "...to direct and support the handling of information throughout its life-cycle ensuring it becomes the right information in the right form and of adequate quality to satisfy the demands of an organization." These services support organizations, groups, individuals and other technical services with capabilities to organize, store and retrieve information (in any format, structured or unstructured) through services and managed processes, governed by policies, directives, standards, profiles and guidelines.
| ID:Service/Purpose | Standard | Implementation Guidance |
|---|---|---|
| 1:Enterprise Search Services: Automated information resource discover, information extraction and interchange of metadata | Mandatory:
Emerging (2014):OpenSearch 1.1 Draft 5 |
The NATO Core Metadata Specification does not define implementation details. However, it describes the format and encoding
of the values captured for each metadata element.
The technical implementation specifications are part of the TIDE Transformational Baseline v3.0, however, Query-by-Example (QBE), has been deprecated with the TIDE Information Discovery specs v2.3.0 and replaced by SPARQL. |
| 2:Enterprise Search Services:
manual information resource discovery, classification marking and file naming conventions |
Recommended:
|
Character codes for permissible Classification Markings will be specified for each Mission Network in the IM Annex of the OPLAN. |
| 3:Enterprise Support Guard Services: General definition of Security and Confidentiality metadata | Mandatory:
|
Services and applications shall implement object level labelling in order to support cross-COI and cross security domain information exchange using common enterprise Support Guard Services (e.g. Cross-Domain Solutions or Information Exchange Gateways) |
426. Metadata shall contain the following elements. Details on the format and encoding of the values for each element are provided in the NATO Core Metadata Specification, AC/322-N(2014)xxxx.
| NCMS element name | XML element name | Obligation | Definition |
|---|---|---|---|
| metadataConfidentialityLabel | ncms:metadataConfidentialityLabel | M | The confidentiality label assigned to the metadata set associated with the resource. |
| originatorConfidentialityLabel | ncms:originatorConfidentialityLabel | M | The confidentiality label assigned to the resource by the originator. |
| creator | ncms:creator | M | An entity primarily responsible for creating the resource, or the originator of the resource. |
| date.created | ncms:created | M | The date on which the resource was created. |
| identifier | ncms:identifier | M | An unambiguous reference to the resource within a given context. |
| publisher | ncms:publisher | M | The entity responsible for making the resource officially available. |
| subject | ncms:subject | M | The topic of the content of the resource. |
| title | ncms:title | M | The title is the official name of a resource. |
| recordsDispositionDate | ncms:recordsDispositionDate | M | The date when the resource will be archived or destroyed. |
| status | ncms:status | M | The current status of a resource (active, semi-active, inactive) |
| coverage | ncms:coverage, with refinements:
ncms:countryCode ncms:geographicEncodingSchema ncms:geographicReference ncms:placeName ncms:region ncms:timePeriod |
O | The temporal and geospatial extent or scope of the content of the resource. |
G.10.3.3. Geospatial Services
427. Geospatial Services deliver network-based access to quality raster, vector and terrain data, available in varying degrees of format and complexity. Geospatial Services form a distinct class of information services through their unique requirements for collecting, converting, storing, retrieving, processing, analysing, creating, and displaying geographic data. The generic nature of Geospatial Services - "organizing information by location" - is interdisciplinary and not specific to any Community of Interest (COI) or application.
| ID:Service/Purpose | Standard | Implementation Guidance |
|---|---|---|
| 1:Geodetic and geophysical model of the Earth. | Mandatory:
NIMA Technical Report 8350.2 Third Edition incorporating Amendments 1 and 2:23 June 2004, Department of Defense World Geodetic System 1984 Its Definition and Relationships with Local Geodetic Systems. |
|
| 2:Electronic format for medium resolution terrain elevation data. | MIL-PRF-89020 Rev. B, Performance Specification: Digital Terrain Elevation Data (DTED), 23 May 2000. | Used to support line-of-sight analyses, terrain profiling, 3D terrain visualization, mission planning/rehearsal, and modeling and simulation. |
| 3:Services to publish geospatial data as maps rendered in raster image formats. | Mandatory:
Emerging (2018):
|
WMTS are to be provided as a complimentary service to WMS to ease access to users operating in bandwidth constraint environments. WMTS trades the flexibility of custom map rendering for the scalability possible by serving of static data (base maps) where the bounding box and scales have been constrained to discrete tiles which enables the use of standard network mechanisms for scalability such as distributed cache systems to cache images between the client and the server, reducing latency and bandwidth use. |
| 4:Services to publish vector-based geospatial feature data to applications | Mandatory:
|
|
| 5:Electronic interchange of geospatial data as coverage, that is, digital geospatial information representing space varying phenomena | Mandatory:
Emerging (2014):
Fading:
|
Web Coverage Service v.1.1.1 is limited to describing and requesting grid (or "simple") coverage.
OGC Web Coverage Service (WCS) Standard Guidance Implementation Specification 1.0 |
| 6:Raster Image Storage Service | Conditional: If all MN Participants confirm that they can ingest DGI/SGI in MrSID_MG3 format.
|
The JPEG 2000 image compression standard offers many of the same advantages as MrSID, plus the added benefits of being an international standard (ISO/IEC 15444). |
| 7:File based storage and exchange of digital geospatial mapping (raster) data where services based access is not possible | Mandatory:
Recommended:
|
This is provided for legacy systems, implementers are encouraged to upgrade their systems to consume OGC Web Services.
In practice, the exchange of large geospatial(raster) data sets between Geo organizations of different Mission Network Contributing Participant is conducted in the proprietary Multi-resolution seamless image database (MrSid Generation 4) format. Data in MrSID format could be transformed to GeoTIFF. |
| 8:File based storage and exchange of non-topological geometry and attribute information or digital geospatial feature (vector) data | Mandatory:
Fading:
Emerging:
NOTE: The current version of the gdb file format is defined via the application programming interface File Geodatabase API 1.3, which is used in several GIS implementations including the open source Geospatial Data Abstraction Library (GDAL). |
ESRI Shapefiles are used by legacy systems and as file based interchange format. Implementers are encouraged to upgrade their
systems based on OGC Web Services.
File geodatabases store datasets as folders in a file system with each file capable of storing more than 1 TB of information. Each file geodatabase can hold any number of these large, individual datasets. File geodatabases can be used across all platforms and can be compressed. They support the complete geodatabase information model and are faster than using shapefiles for large datasets. Users are rapidly adopting the file geodatabase in place of using shapefiles. |
| 9:Geospatial Coordinate Services: general positioning, coordinate systems, and coordinate transformations | Recommended:
|
|
| 10:GeoWeb Service Interface to GIS Servers: | Recommended:
|
There are implementations of the Open Esri GeoServices REST specification from various other vendors. The REST API may be used for an easier to implement and rich interface to the server side GIS capabilities. Functional Services that support this interface may take advantage of this interface. |
| 11:Geo-Analytical Functionality as a Service: | Recommended:
|
Instead of retrieving all required spatial data in order to analyse it in a fat client, clients are encouraged to invoke the analytical processes where the data resides so that only the analytic result needs to be transmitted from the server to the client. |
| 12:Geospatial Coordinate Services: identifying Coordinate Reference Systems (CRS): | Fading:
Recommended:
|
The European Petrol Survey Group maintains the most comprehensive and accurate register of international geodetic codes and parameters for CRS. To identify the CRS for the exchange of geospatial data a standard naming convention and reference repository is required |
| 13:3D Perspective Viewer as a GeoWeb-Service: | Recommended:
|
|
| 14:Geospatial Frames of Reference: |
Conditional: Only to be used for operational-level air-to-ground coordination, deconfliction, integration, and synchronization. GARS shall not be used
|